FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
IPSec is a protocol used to secure data transmissions between two devices. It was developed as part of the Internet Engineering Task Force (IETF).
IPSec is a security protocol that protects IP traffic from eavesdropping and tampering. This means that it encrypts messages sent over networks, making it difficult for hackers to intercept communications.
IPSec works by using public key cryptography to create a pair of keys called symmetric keys. These keys are used to encrypt and decrypt packets of information.
When a device wants to send sensitive information to another device, it uses its private key to encrypt the message. Then, it sends the encrypted packet to the recipient.
Once the recipient receives the packet, he/she uses his/her public key to decrypt the message. Only someone with access to both the sender’s and receiver’s public keys will be able to read the message’s contents.
The beauty of IPSec is that it doesn’t require any special hardware to work. Any computer running Windows XP SP2 or later can run IPSec. And because it’s open source, anyone can download and install IPSec on their own computers.
Check out a simple explanation and details if you want to know more about how IPSec works.
What is IPsec?
IPsec is a protocol used to encrypt data and authenticate the sender of the data. This makes it possible to securely send sensitive information like credit card numbers over the Internet.
The acronym “IPsec” is short for Internet Protocol Security. This refers to the technology that allows us to send e-mail securely across the Internet.
You might use IPsec to protect your personal banking information, like your credit card numbers, or you could use it to help protect your corporate communications.
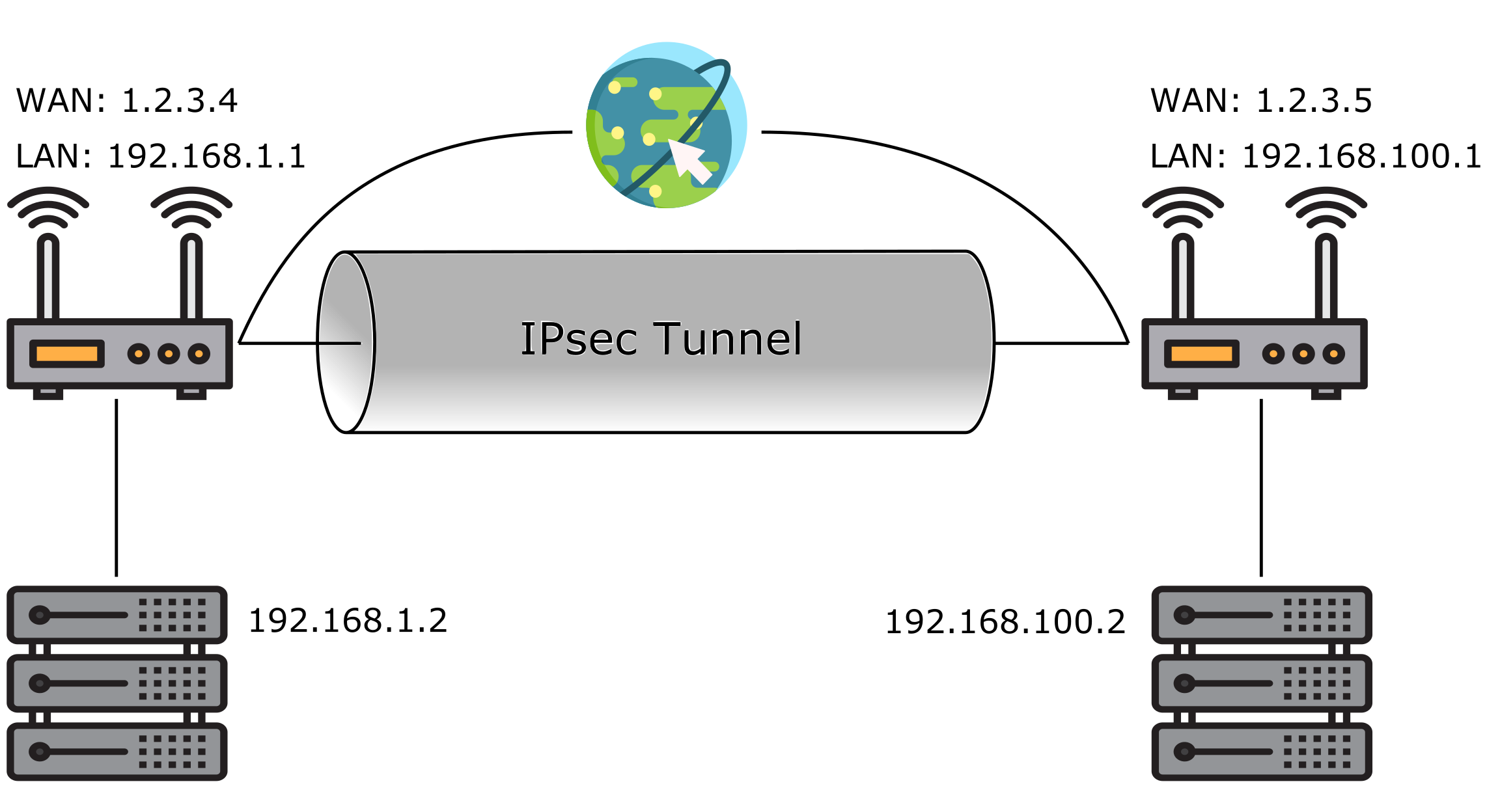
In other words, IPsec is a group of technologies that help ensure that data transmitted across networks are safe. Encrypted traffic is usually protected via IPSec tunnels.
These tunnels are established by sending messages between entities called peers. A peer is a device on either side of the connection that uses IPsec to communicate securely.
In addition to securing data, IPsec also authenticates the sender of a packet. This prevents one person from pretending to be someone else while communicating.
The IP Security Association (IPsec), developed by the IETF, is a standard for implementing security solutions.
IPsec protects against malicious eavesdropping and tampering. It creates a tunnel between two points, known as peers. Each peer contains a pair of cryptographic algorithms.
One algorithm transforms data into something that looks like gibberish to anyone trying to intercept it. The second algorithm turns the gibberish back into readable text.
IPsec uses a variety of algorithms for encryption and authentication. The Advanced Encryption Standard (AES) and the Message Digest 5 (MD5) algorithms are the most common. AES is the preferred encryption algorithm, which is more secure than MD5.
IPsec employs many different modes for encrypting data. The most common are Transport Mode and Tunnel Mode. Transport Mode encrypts only the data portion of each packet, while Tunnel Mode encrypts the entire IP packet.
Tunnel Mode is typically used to secure communications between two networks, while Transport Mode is more commonly used to secure communications between a host and a network.
IPsec can be used with other security protocols, such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL).
History of IPsec
IPsec is a suite of transport layer security protocols developed during the 1990s to secure communications over the Internet.
While “IPSec” is commonly used to refer to the entire suite of protocols, the acronym stands for “Internet Protocol Security,” meaning that IPSec refers specifically to one of those protocols.
The original version of IPSec was designed to provide encryption for internet communications; it was originally called IKE (standing for “internet key exchange“) and later evolved into ISAKMP (standing for “ISDN Authentication Key Management Protocol”).
In 2004, IPSec was standardized as RFC 2401 and became part of the Internet Engineering Task Force (IETF). IPSec is widely used to protect VPN connections, remote access connections, and other types of network communication.
What mode of operation, protocols, algorithms, and keys are used in IPsec?
Internet Protocol Security (IPsec) is a suite of security protocols used to authenticate and encrypt communications over the Internet.
IPsec is a layer-3 security protocol that uses cryptographic security services to protect communications at the IP layer.
IPsec uses a combination of protocols, algorithms, and keys to provide security for data in transit.
IPsec supports two modes of operation: transport mode and tunnel mode. Transport mode secures communications between two hosts, while tunnel mode secures communications between two security gateways.
IPsec can be used with a variety of encryption algorithms, including Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
IPsec uses many different protocols to provide security. The most commonly used protocols are Authentication Header (AH) and Encapsulating Security Payload (ESP).
AH provides authentication and integrity for data, while ESP provides confidentiality, authentication, and integrity. AH and ESP can be used together or separately.
IPsec also uses many different algorithms to provide security. Message Digest 5 (MD5) and Secure Hash Algorithm 1 (SHA-1) are the most commonly used algorithms. MD5 is used for data integrity, while SHA-1 is used for data authentication.
IPsec uses a variety of keys to provide security. The most commonly used are preshared, public, and private keys.
Preshared keys are used to authenticate communications between two hosts. Public keys are used to authenticate communications between two security gateways. Private keys are used to encrypt data.
IPsec is a complex security protocol used to authenticate and encrypt communications over the Internet. IPsec uses a combination of protocols, algorithms, and keys to provide security for data in transit.
How does IPsec work? (A simple explanation)
IPsec is one of the most important protocols to secure data traveling across networks. It is so important that it is included in almost every modern network device.
Despite its importance, many people don’t fully understand how it works.
Basic Concepts
First, let us start with some basic concepts. A packet is simply a piece of information sent between two devices. Packets are often referred to as bits moving along wires because that is exactly what they are.
Each packet contains a source address, a destination address, and a payload. Source addresses indicate where the packet came from; destination addresses identify where the packet is going, and the payload contains whatever the sender wants the recipient to see.
The Internet Protocol (IP) specifies how each packet travels from one computer to another. Every computer on the Internet uses IP to communicate with every other computer.
When a person types “www.google.com,” her computer sends out a request containing her IP address, asking for webpages hosted on Google’s servers. Those servers send the requested webpage back to the original computer, which displays it to the user.
The role of IPsec
IPsec is a protocol designed to protect the confidentiality of data traveling between computers. To do this, IPsec encrypts the data in transit, ensuring that no one else can read it. If someone intercepts the traffic, he cannot read the contents without knowing the encryption key.
In addition to protecting the data itself, IPsec also protects against attacks known as man-in-the-middle attacks.
These occur when someone pretends to be either the server or the client, allowing him to eavesdrop on communications. By doing this, he can learn things like passwords, credit card numbers, etc., which could allow him to commit fraud later.
IPsec creates a virtual tunnel between the server and the client to prevent such attacks. Data flows through this tunnel, protected by strong encryption algorithms. Once inside the tunnel, the data is encrypted again, making it unreadable to anyone outside the tunnel.
Mode of Operation
IPsec supports three main modes: transport, tunnel, and ISAKMP. Transport mode is used to provide end-to-end protection for individual applications. Tunnel mode provides authentication and integrity checking for VPN connections.
Finally, ISAKMP mode allows organizations to establish secure communication channels among themselves.
The most common mode of operation is transport mode, where both ends of the connection use IPsec to negotiate encryption keys and establish a secured tunnel.
Transport mode uses public key cryptography, meaning each endpoint generates a unique set of cryptographic keys and exchanges them during negotiation.
Once the keys are exchanged, the traffic is encrypted and transmitted securely. When the receiving endpoint receives the traffic, it uses the negotiated keys to decrypt it, ensuring that no one else can intercept the communication.
There are three main types of IPsec tunnels: IKEv1, IKEv2, and ESP. IKE stands for Internet Key Exchange, the protocol used to negotiate the keys for the IPsec tunnel. IKEv1 is considered insecure because it doesn’t authenticate the identity of the communicating parties.
Therefore, anyone can impersonate another party without being detected. IKEv2 addresses this issue by providing mutual authentication, ensuring that only the correct parties can communicate.
ESP stands for Encapsulating Security Payload, a newer protocol developed specifically for VPNs. ESP allows for better performance than IKEv1/IKEv2 since it doesn’t require exchanging large amounts of data. Instead, ESP encodes the entire payload inside UDP datagrams, allowing for very small packet sizes.
Process Involved in IPsec
The first step in IPsec is establishing a secure connection between two hosts. To do this, both parties must agree upon a secret key, known as a shared secret. For example, if Alice wants to send a packet to Bob, she encrypts the packet using her public key, which she publishes to everyone.
Only someone with access to the corresponding private key — Bob — can decrypt the packet using his public key. If Bob gets the packet, he knows it came from Alice because only she could have encrypted it using her public key.
Once the initial handshake is complete, the two hosts exchange messages over a second channel, known as Phase 0. These messages contain authentication information, including a cryptographic hash, which proves that the host claiming to be Bob is Bob.
After this phase is completed successfully, the two hosts exchange packets over a third channel, referred to as Phase 1. This is where the actual encryption takes place.
In general, Phase 1 consists of three parts: Encapsulation Security Payload (ESP), Authentication Header (AH), and Key Exchange (KE). ESP contains the payload, AH contains the authentication information, and KE provides the keys used to encrypt and authenticate the traffic.
There are several types of KE protocols, depending on what kind of secrets are being exchanged. Each mode of operation uses a different method to generate the keying material.
IPsec offers four distinct modes of operation, which are differentiated based on the type of keying material being used. All four modes use the Diffie-Hellman key agreement to derive keying material. However, the way the keying material is generated differs among the modes.
What is the difference between IPsec tunnel mode and IPsec transport mode?
IPsec tunnel mode connects two dedicated routers, with both routers acting as ends of a virtual “tunnel.” Each router acts as one end of the tunnel; it encrypts the entire IP packet and sends it along, while the second router decrypts the packet and forwards it onward.
In IPsec tunnel mode, IPsec adds a layer of encryption over the original IP header, including the source address and port number. This makes it possible for intermediate routers to see the original IP header but prevents them from seeing the destination.
Transport mode differs from tunnel mode because the packet’s payload is encrypted. However, the original IP header is still visible. For example, when you use TCP/IP, the original IP header includes the destination address, making it possible for intermediate routers (and even computers) to see the destination.
The original IP headers are not protected with transport mode, allowing intermediaries to see the destination. To protect the original IP headers, you must use tunnel mode.
Difference between IPsec vs. TLS/SSL
The Internet Protocol Security (IPsec) protocol provides encryption and authentication capabilities for communications across multiple networks. IPsec works at the third layer of the Open Systems Interconnection (OSI) model.
This means that it is positioned within the network layer, which allows it to encrypt and authenticate data packets sent between hosts on a local area network (LAN), wide area network (WAN), or even across the Internet.
TLS/SSL operates at the second layer of the OSI model, the transport layer. This means that it encrypts and authenticates data packets sent between endpoints on a LAN, WAN, or even across the Internet but does not secure the underlying network itself.
Because IPsec and TLS/ SSL operate at different layers, they perform slightly different functions. While both are designed to protect against eavesdropping and man-in-the-middle attacks.
Why should you use IPsec?
If you want to use IPsec for securing your network traffic, there are some things you need to know.
IPsec is one of the most common ways to encrypt data over a network. But, like many technologies, it isn’t perfect, and it does come with certain drawbacks.
So, while it might make sense for some networks, it’s probably not something you should rely on exclusively.
The problem with IPsec is that it doesn’t work well without a third party. For example, if you’re trying to connect to a remote server, you won’t be able to do it directly because IPsec needs to negotiate a key with the remote server.
This negotiation process takes place over the Internet, which leaves your computer vulnerable to attacks.
Another problem with IPsec is that it uses Microsoft’s proprietary protocol, MS-CHAPv2. This means that you cannot easily switch to another encryption method.
You could try switching to another encryption protocol, such as SSH, but unless you’re willing to pay for a commercial product, you’d have no choice but to stick with IPsec.
Finally, IPsec is very difficult to set up. Multiple steps are involved in configuring it correctly, and even experienced IT professionals often struggle.
So, if you’re looking for a way to encrypt your network traffic, IPsec is worth considering.
However, it’s important to understand that it has its limitations. And you shouldn’t just assume that it’s suitable for every situation.
Conclusion
IPSec is a very important security protocol that is widely used in VPNs. It ensures that data is not tampered with or intercepted while in transit.
IPSec works by authenticating and encrypting each packet of data that is sent. This makes it virtually impossible for anyone to read the data or make changes.