FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
You would be wondering how one computer can communicate with other computers in a network. A network can consist of two computers, or it can be lots of computers.
So, which technology is involved in any communication in a network?
Computers can perform any communication in a network only when they agree to a set of rules applicable to every computer.
The set of rules that governs the whole communication in a network are called protocols.
So, the standardized rules that allow any computer in a network to communicate with each other are called Transmission Control Protocol/ Internet Protocol (TCP/IP).
TCP/IP can help in developing communication between two computer system, which make it possible for you to browse any websites, send emails, and start online streaming.
It doesn’t matter which part of the world your computer is located, what it was made-up and in which language it is communicating.
The only thing that matters is whether the networking connection is well established or not. If one part of the connection is throwing any error, then the communication will not end up successfully.
To understand whole communication, which is running in the background, you need to know the functioning of TCP/IP.
What is TCP/IP, and how it works?
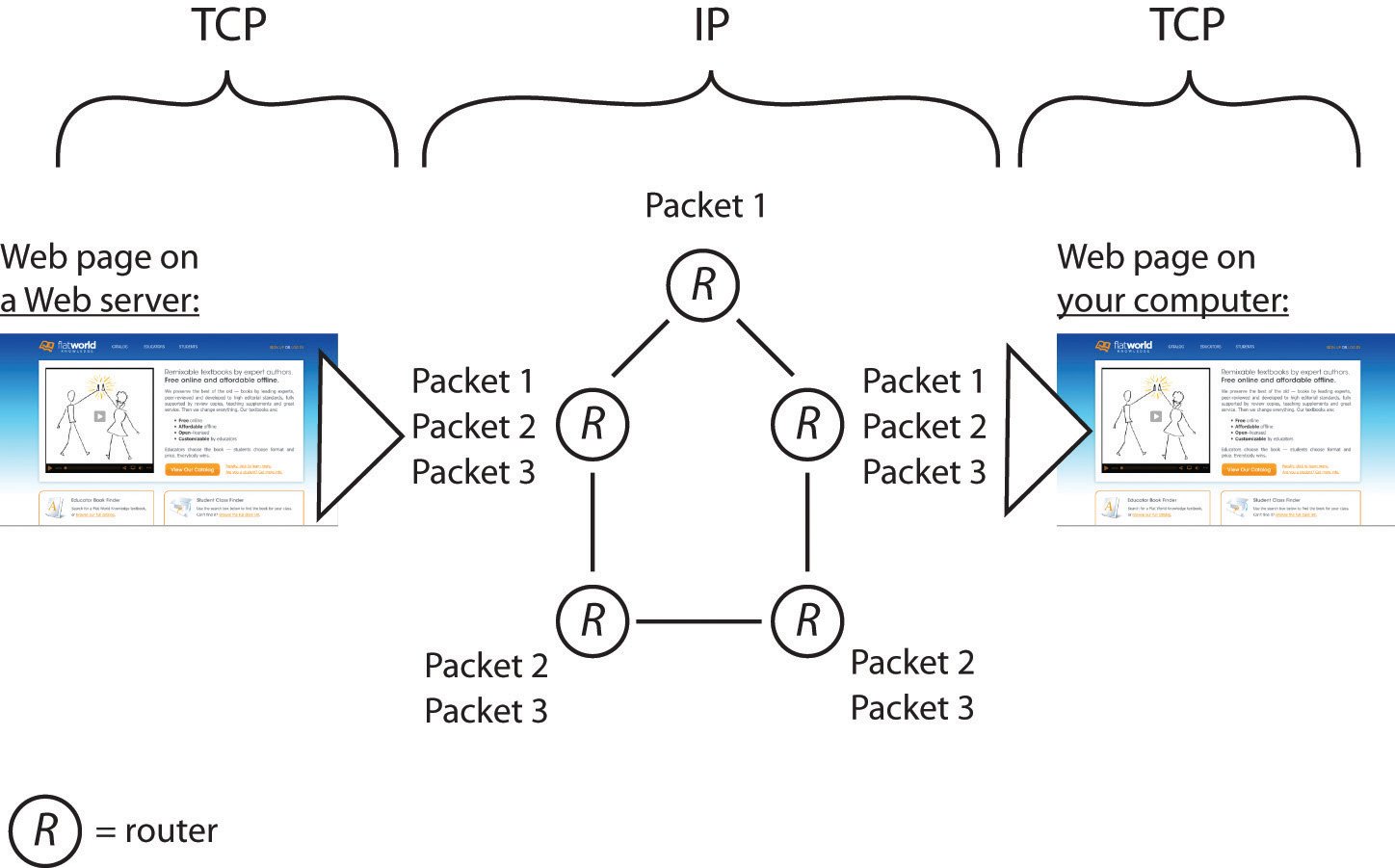
TCP/IP is a communication protocol that establishes a connection with another computer and ensures that the packets are sent and received successfully.
Every message or data that is sent in a network breaks into multiple packets. Each packet is traversing with a different path, but all the packet will reach the same destination.
When all the packets are collected in the receiver end, they are assembled to form meaningful information.
Difference between TCP and IP
IP termed as Internet Protocol. Its work is to establish a connection by identifying another computer of the other end and then deliver the packets to the target destination.
Internet protocol identifies another computer through an address system known as an IP address. An IP address is a prime way to identify any computer in the network.
But, Internet Protocol does only one part of the job. Another part of the job is done through Transmission Control Protocol (TCP).
The Transmission Control Protocol handles the ordering and delivery of the packets and manages the error correction during communication.
Both TCP and IP assist each other during the transmission of data from source to destination. That’s why it is known as TCP/IP, and the whole process is based on a model known as the TCP/IP model.
What is the TCP/IP model, and how does it work?
TCP/IP model was first developed by the U.S. Department of Defense to transfer data from one computer to another computer.
How TCP/IP work?
The whole process of TCP/IP takes several steps to ensure the successful delivery of the message from one computer to another computer.
The message or data was not sent at once; instead, it is divided into multiple small pieces, and each piece is known as a packet. So, whenever you sent any message, it was first divided into multiple packets.
Each packet takes its route and reaches the expected destination. In the receiver end, the packets are reassembled to form a complete message.
If any packet was undelivered or failed to deliver, it will be re-sent from the other end. If they found congestion in one route, they will automatically take another route to complete the delivery process.
So, for the successful delivery of data, the whole process of the TCP/IP model is divided into multiple layers. Each layer has its functionality, and one layer depends on another layer.
After the message is received, it has to pass through a set of layers to reach the destination, and the same process will continue in a reverse order to reassemble the data and represent it to the recipient.
The whole purpose of dividing into multiple layers is to keep things straightforward and standard. That’s why any computer or server in a network has to follow the standard procedure to communicate.
TCP/IP Analogy
We can also compare the TCP/IP model with a real-life example like a car manufacturer, who follows the standard procedure during manufacturing, deciding on where should be the pedal, brake, and clutch in a car.
The benefit of dividing the TCP/IP model into multiple layers is to deal with each layer separately. If any layer needs an upgrade in technology or some improvement, then there is no need to change the entire system; instead, focus on a particular layer.
Let’s understand what the four-layer of the TCP/IP model is. And how these four layers work together to achieve the successful delivery of the message.
The four-layer of the TCP/IP model
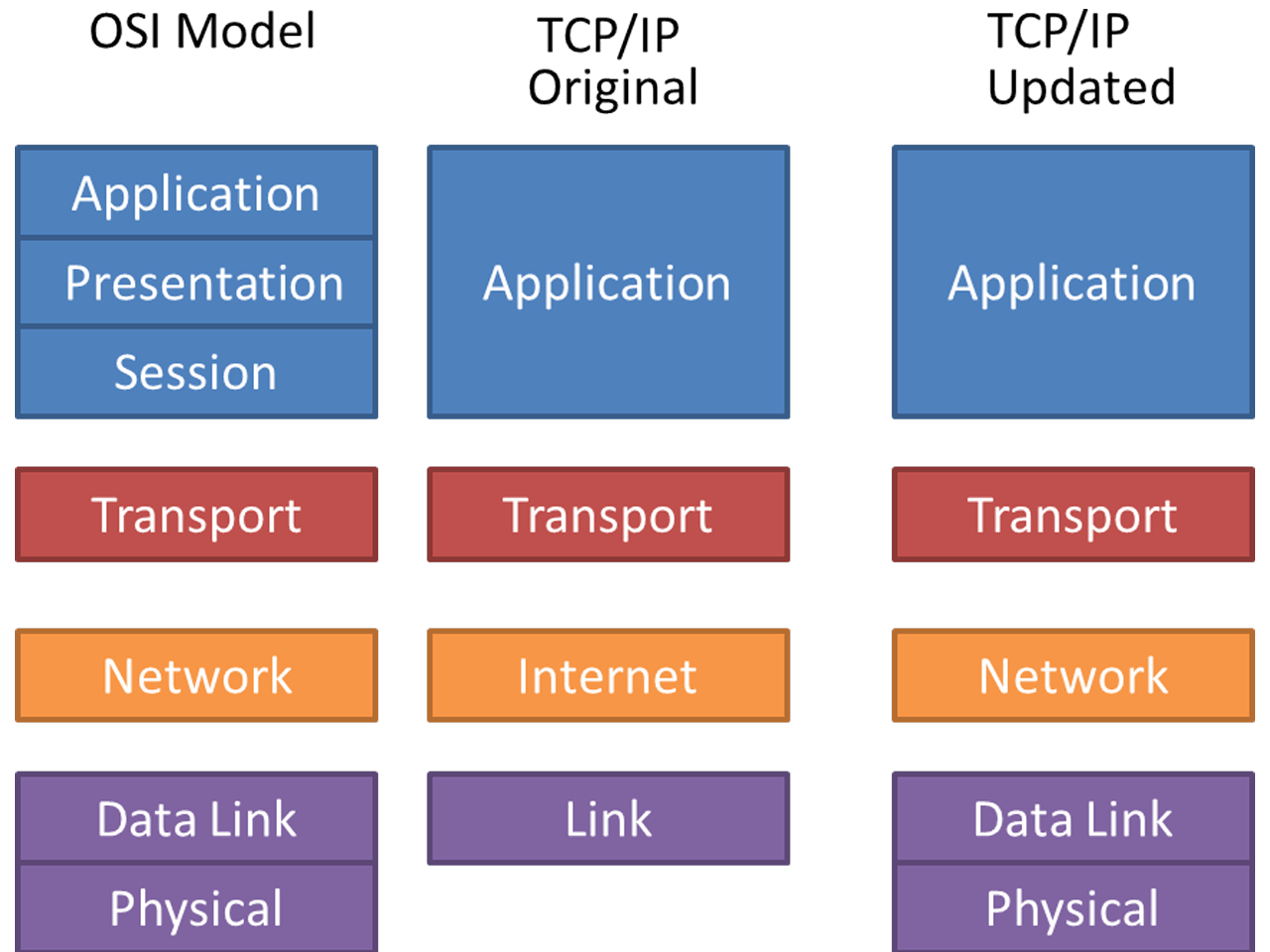
The TCP/IP model’s main functionalities are based on the theoretical OSI model. In the OSI model, there was a seven-layer whereas, in the TCP/IP model, it shrinks to four-layer.
The four-layer of the TCP/IP model includes
- Application layer
- Transport layer
- Internet layer
- Network Interface layer.
When the message was sent using an application from your computer, it has to pass through four-layer from the application layer to the network interface layer.
After that, it will get transmitted over the network and reaches the destination computer. Finally, at the destination, it will work in reverse order from the network interface layer to the application layer.
During the transmission of data from the application layer to the network interface layer or vice versa, each layer adds its header to the packet.
When the packet reaches the destination computer, the header is retrieved and handled by the receiving computer. The packet size depends on the size of the content and the size of each header added in different layers.
Application Layer
The application layer of the TCP/IP model contains lots of application layer protocol, and each protocol is used for a different type of communication.
To establish network communication for a different purpose, we need a software program or application to follow the application layer protocols.
So, the software program or application uses these types of application layer protocols to request different kinds of actions.
Some of the standard application layer protocols are:
- HTTP, HTTPS – Protocol use for web browsing
- FTP, TFTP, NFS – File transfer protocol
- SMTP – Protocol for sending email messages
- POP3 – Protocol for receiving email messages
- IMAP – Protocol for managing email messages on the server
- Telnet, rLogin – Protocol for accessing remote computers
- SNMP – Protocol for network management
- DNS – Protocol for finding IP address assigned to web addresses
- IRC – Protocol for online chats
Each of the application layer protocols will have different input data and can generate different queries. All these data are sent to the next layer, which is the transport layer.
The transport layer has nothing to do with the content of the application layer, and it will process every data in the same way.
Before moving to the transport layer, we need to understand what makes communication possible between the application and the transport layer.
Internet socket
An Internet socket is an endpoint of the two way communication between two applications running over a network.
In short, we can say that Socket plays a crucial role in keeping any communication over a network neat and tidy.
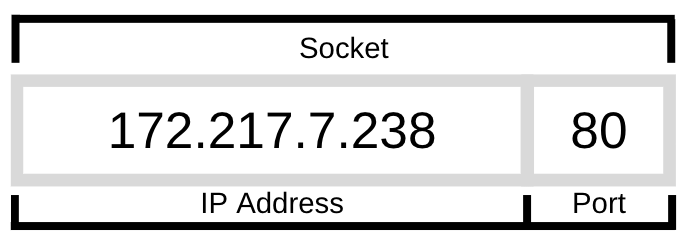
To understand Socket, we need to know that socket consist of three things; an IP address, a port number, and a transport layer name. Let’s go through one by one.
IP address
An IP address is one of the foremost things to start any communication in a network. It identifies your computer in a network by using the Internet Protocol (IP) for communication.
When you type in any website in a browser and hit enter, you send a request to the server along with your IP address. So, the request received by the server will know where to send the content.
From your computer, you are not only using a browser, but also several other applications, and there could be so many requests at the same time.
But how all these requests and applications are identified by the other end of the computer.
Different programs or applications generate many types of requests. So to make every request in a network standard, another technology was introduced known as port.
Port
The port is a 16-bit number that identifies your specific application or service in a computer that wants to connect to a network.
Here, when we talk about port, we talk about software port, not hardware port.
So, the IP address identifies your computer, and port number identifies the specific application on your computer.
The port number can be assigned by your operating system automatically, or the user can manually use it.
For popular application layer protocols, the port number can be set as default.
The well-known default port number for different application layer protocol are: HTTP uses port number 80, HTTPS uses port number 443, FTP uses port number 21, SMTP uses port number 25.
Likewise, we have a different port number for different application layer protocols.
Let’s understand the whole thing with a simple example.
google.com: 172.217.7.238:80
The google.com website is residing in a web server with an IP address 172.217.7.238. In a web server, 80 is the port number from where the content can be retrieved. The type of content depends on the application layer protocol, like HTTP.
If any website uses a specific port number other than the default port number, then you have to mention along with the domain name.
Like, https://example.com:8080
You can follow the guide for more details on Ports, IP address, and Socket.
Transport layer
The transport layer is the next in the TCP/IP model, which receives a message from the application layer.
The transport layer work is to divide the message into multiple small packets and then add a header and send it to the internet layer.
Similarly, in the reverse direction, when data is received from the internet layer, it passes to the application layer.
The header of the transport layer contains much information along with the port number of the source and target destination.
The transport layer uses port numbers to determine what kind of message is inside the packets and which application layer protocol should receive them.
For instance, if the port number is 25, then it will reach most probably to SMTP protocol. Now, the SMTP will provide the data requested by the email client.
The two main transport layer protocol is used in the process are:
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
The Transmission Control Protocol, in short TCP, is the most common and reliable protocol between two hosts.
The most common application layer protocols that use TCP are HTTP, HTTPS, FTP, SMTP, and Telnet.
The User Datagram Protocol, in short UDP, is the fast and connectionless protocol.
It does not develop any relation with the receiver end, and also it is not reliable like TCP because there is no guarantee your packets would reach the receiver.
The most common application layer protocols that use UDP are DNS, DHCP, TFTP, SNMP, VOIP, and RIP.
Internet Layer
The Internet Layer, also called the network layer, controls the movement of packets around the network boundaries.
The internet layer adds another header to the packet when it is received from the transport layer. The most important fields in the header are the IP address of the source and destination of the two ends.
The internet layer uses some of the most important protocols. The three main internet layer protocols are:
IP (Internet Protocol) – Internet Protocol work is to identify the IP address and responsible for the delivery of the packet to the destination.
ARP (Address Resolution Protocol) – The address Resolution Protocol work is to find out the MAC address of the device from the IP address.
ICMP (Internet Control Message Protocol) – The Internet Control Message Protocol identifies network problem associated with small packets called Datagrams, and send back to the sender with an error message.
Network Interface layer
The Network Interface layer (also called Data Link Layer or Physical layer or Network access layer) is the physical interface between the host computers and the network hardware.
This layer is responsible for the transmission of data between two devices of the same network.
It handles the network hardware of the computer, which is used for sending or receiving data using the wireless network, Ethernet cable, network interface card, device driver, and so on.
Its main focus is to establish communication between the network card and networking hardware.
It also defines how the data should be sent in the network, which includes how bits should optically be signaled by network hardware.
Is your data safe and secure?
The confidential data in a network is not safe. When you are connected to public WiFi, then you are more vulnerable to the eye of hackers or government agencies.
The website administrator or hackers are tracking most of the stuff you would be doing online.
Sometimes, it may be possible that they want to read your online behavior and feed with relevant ads that may be profitable to them.
But, not everyone is okay to share their personal information and online behavior.
So, when data is transmitted over a network, it may get leaked.
To protect your data in a network, you need to encrypt it. In your home WiFi, you have to turn on encryption in your router setting for basic protection.
But, if you are in public WiFi or want the data to be completely secure, then you have to use Virtual Private Network (VPN).
A VPN will ensure that your data is completely safe, secure, and encrypted before moving into a network. The good VPN doesn’t keep any logs, which makes it impossible to trace your activity online.
Try NordVPN – the world’s best VPN for security and privacy.
Does TCP/IP support all types of IP address?
TCP/IP support all type of IP address. There is mainly two types of IP address.
- Public IP address – It is provided by ISP and is used to communicate outside of the network.
- Private IP address – It is a local IP address within a network. It is a device IP address.
The public IP address is further divided into two categories.
Dynamic IP address – It changes with a certain period, and most of the ISP provides you with a dynamic IP address.
Static IP address – It remains unchanged and mostly used by companies who are maintaining a server or local network.
Again, the IP address is divided into two versions. The current version of the IP address, which most of them are using is IPv4.
But, with the increasing number of devices, TCP/IP is running out of IP address. So, the new version of the IP address is created, which is called IPv6.
How to find the TCP/IP address?
The TCP/IP address is sometimes needed to configure your network. It requires most when you are in a local network.
Every device has a different method to find the IP address. You can find here the most detailed guide on how to find the IP address on your computer, phone, and router.
How to protect your TCP/IP address?
TCP/IP address is vulnerable when you are transmitting data in a network. If it is important, then it needs to be protected and secured in a network.
Nord VPN not only protects your TCP/IP address from prying but also gives an extra layer of security and privacy in a network.
Conclusion
TCP/IP is the builtin standard for the majority of computers. It is the most commonly used protocol by the vast majority of the population without knowing it.
The basic concept of TCP/IP is helpful in the configuration of the application manually. Since it comes well configured with your system, you don’t have to do anything.
On some occasions, you may need to hide your IP address to surf the web anonymously. If you want to secure your network connection from eavesdropping, then use a VPN like NordVPN.