FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
Internet Key Exchange version 2 (IKEv2) was developed by the Internet Engineering Task Force (IETF). It is used in many protocols, including IPsec VPNs, S/MIME, SSH, TLS, IPSec, RADIUS, etc.
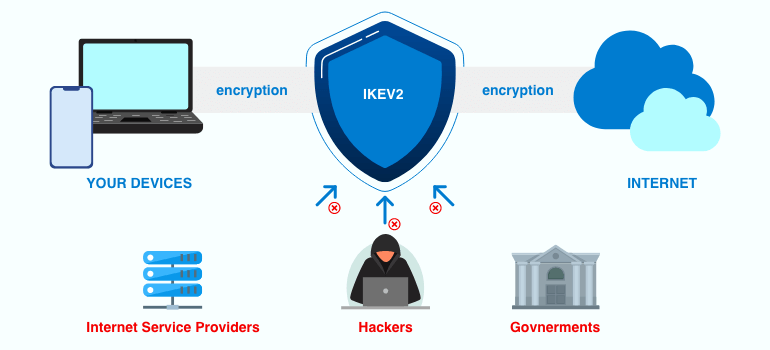
In short, IKEv2 allows two parties to exchange keys over insecure channels such as the Internet securely. This makes it possible to encrypt data without having to trust each other.
IKEv1 was the first Internet Key Exchange protocol version and has been around since 1994. It was designed to provide secure communications between hosts over public networks like the Internet.
In recent years, however, we’ve seen a new standard called IKEv2. This more unique protocol provides many improvements over its predecessor, including faster speed, improved security, and compatibility with IPv6.
IKEv2 is currently used by major companies such as Google, Microsoft, Amazon, and Netflix. But most importantly, it’s also becoming increasingly popular among home users who want to encrypt their connections.
This article will explain exactly what IKEv2 is, why it’s important, and how it works.
What is IKEv2?
Internet Key Exchange version 2 (also known as IKEv2) is one of the most important protocols used in VPN technology today. This protocol enables secure communications between devices such as smartphones, computers, tablets, servers, routers, etc.
IKEv2 merges two existing technologies into one: IPSec and OpenVPN. This allows you to use either of those protocols individually or combine them together.
The IKEv2 protocol defines how to establish secure connections between clients and servers. It does this by defining the steps required for establishing a secure connection. These steps include exchanging cryptographic keying material (keys), negotiating encryption algorithms, and authenticating each other.
IKEv2 negotiates and authenticates IPsec SAs (security associations), which are needed to establish a secure connection between two parties. You can think of it like a handshake; both sides exchange information about each other and agree upon how to communicate securely.
In addition, IKEv2 supports authentication mechanisms such as certificates, public key infrastructure (PKI), and Kerberos.
The first generation of IPsec, IPSec, was developed in 1988 by Cisco Systems, Inc., and later adopted by many other companies. In 2001, Microsoft Corporation introduced IKEv1, which is still widely used today. However, IKEv2 is gaining popularity because it offers better performance and scalability.
NordVPN and others call this combination “IKEv2/IPsec.” They say it provides faster speeds and more robust encryption than older versions of IPsec.
Why does IPsec work with IKEv2 to establish a secure connection?
IKEv2 is a protocol used to negotiate a secure connection between two devices. This protocol is often called Internet Key Exchange version 2 (IKEv2).
When you connect to a Wi-Fi network, you use IKEv2 to establish a secure connection with the router. Once the connection is established, you send information about yourself, such as your username and password, over the encrypted channel.
IPsec is another encryption protocol that operates on top of IKEv2. It is designed to encrypt traffic flowing between two networks.
For example, you might want to protect traffic sent between your home and office networks. Using IPsec, you can set up a virtual tunnel that protects both directions of communication. You can even combine IKEv2 and IPSec to make a hybrid solution to increase efficiency.
The combination of IKEv2 with IPsec is called IKEv2/IPSec. It is welded to IPSec because they run in the same software environment.
Both protocols operate in the user space, where they can access data stored on hard drives. They also work in the kernel, the deepest layer of the operating system. This makes them faster than other methods of securing communications.
What’s the difference between IKEv1 and IKEv2?
IKEv1 and IKEv2 are both Internet Key Exchange protocols, which are used to establish secure communications over the Internet. But while IKEv1 is a legacy protocol, IKEv2 is newer and better. Here are the four most important differences between the two protocols:
• IKEv2 runs much faster and more efficiently because it uses fewer resources.
• IKEv1 requires a lot of bandwidth, whereas IKEv2 uses less.
• IKE v2 supports Network Address Translation (NAT), which allows computers behind a router to use IP addresses outside the local network without revealing those addresses to others.
• IKE version 2 is backward compatible with IKEv1. This means that clients and servers that support IKEv1 will continue to work with IKEv2.
The first version, IKEv1, is designed to support virtual private network (VPN) applications. This protocol allows two hosts to negotiate a shared secret key that can be used to encrypt traffic between them.
In addition to supporting VPNs, IKEv1 can be used to build remote access solutions such as IPSec gateways, firewalls, intrusion detection systems, and tunneling devices.
The second version, IKEv2, is intended primarily for host-to-host communications within an enterprise.
Unlike IKEv1, which requires a third party to provide authentication and encryption keys, IKEv2 uses public/private key pairs to authenticate peers and encrypt data streams.
As a result, IKEv2 supports peer-to-peer communications without requiring additional infrastructure.
Benefits of the IKEv2/IPSec Protocol
The IKEv2/IPSec protocol is a powerful tool that can be used to protect your online privacy and security.
The IKEv2/IPSec protocol allows us to establish a secured tunnel between two entities. When we talk about VPN, we usually think of encrypted traffic at the IP level. But there are many ways to encrypt data; some work better than others.
For example, IPsec provides three levels of encryption: transport mode, tunnel mode, and main mode.
Transport mode ensures that the packet headers are protected, while tunnel mode protects the payload itself. The Main mode does both.
Here are some of the benefits of using this protocol:
1. IKEv2/IPSec is a very secure protocol.
This protocol uses strong encryption algorithms to protect your data from being intercepted and read by third parties. Additionally, IKEv2/IPSec uses various authentication methods to ensure that only authorized users can access your data.
2. IKEv2/IPSec is very fast.
IKEv2/IPSec protocol is designed to be very efficient, so it can provide a fast and responsive experience when you’re using it to browse the web or online access services.
3. IKEv2/IPSec is very flexible.
IKEv2/IPSec protocol can be used with various devices and operating systems, so you’ll be able to find a solution that fits your needs. Further, IKEv2/IPSec can also be configured to work with various networking environments.
4. IKEv2/IPSec is very reliable.
This protocol is designed to be robust and resistant to failure, so you can be confident that your data is safe and secure.
5. IKEv2/IPSec is easy to use.
IKEv2/IPSec protocol is designed to be easy to set up and use, so you’ll be able to get started quickly and easily. Moreover, IKEv2/IPSec has various tools and resources to help you troubleshoot and configure it.
Disadvantages of the IKEv2/IPSec Protocol
IKEv2/IPSec is a secure communications protocol that uses a variety of security mechanisms to protect data. It is often used in virtual private networks (VPNs) and is supported by many security products.
However, IKEv2/IPSec has many disadvantages that should be considered before using it.
1. IKEv2/IPSec is a complex protocol.
IKEv2/IPSec is a complex protocol that can be difficult to configure and troubleshoot. It requires a good understanding of networking and security concepts to configure it properly.
2. IKEv2/IPSec is not widely supported.
IKEv2/IPSec is not as widely supported as other VPN protocols, such as PPTP and L2TP/IPSec. This can make it difficult to find compatible VPN clients and servers.
3. IKEv2/IPSec can be slow.
IKEv2/IPSec can be slower than other VPN protocols due to the security mechanisms’ overhead. This can make it less than ideal for use in high-speed networks.
4. IKEv2/IPSec is not always compatible with NAT.
IKEv2/IPSec is not always compatible with Network Address Translation (NAT) devices. This can make it difficult to use in some network environments.
5. IKEv2/IPSec can be difficult to configure.
IKEv2/IPSec can be difficult to configure due to the many available options and settings. This can make it time-consuming to set up and can also lead to configuration errors.
IKEv2/IPSec is a secure communications protocol with many advantages and disadvantages. It is important to understand these before deciding to use them in your network.
Is IKEv2 VPN Secure and safe?
Yes, IKEv2 does support 256-bit encryption, which is considered secure enough for most people. But what about the rest of the features? Let’s take a look at some of them.
IKEv2 supports cipher suites: AES, 3DES, ChaCha20, Camellia, SEED, Twofish, RC4, Blowfish, DESede, and Arcfour. This list isn’t exhaustive, but you’ll find plenty of options.
What’s more, IKE v2 supports Perfect Forward Secrecy (PFS), which means that even if someone somehow manages to break into one of your encrypted connections, he still won’t be able to decrypt previous sessions.
The protocol uses mutual authentication, meaning that both parties must prove their identities before starting any communication. In addition, IKEv2 includes a mechanism called Mobility Encapsulation Mechanism (MOBIKE), which allows mobile devices to seamlessly switch between different access points without losing connectivity.
And finally, IKEv2 supports Certificate Validation, which ensures that the certificates used are legitimate.
So yes, IKEv2 seems pretty good. Well, there’s always something else to consider.
Is IKEv2 Fast?
IKEv2 is commonly known as the Internet Key Exchange version 2 protocol. It is considered one of the most secure VPN protocols, used by many large companies like Cisco Systems, Juniper Networks, Microsoft, and others.
IKEv2/IPsec security features include perfect forward secrecy, data integrity, authentication, encryption, and key management. However, while it does offer some great benefits, it doesn’t always deliver the best performance.
As the name suggests, IKEv2 uses IPsec technology to provide security over a network connection. This is done by encrypting data packets sent across the Internet, ensuring that no third parties can intercept traffic without permission.
However, what makes IKEv2 different from other VPN protocols is its ability to offer better performance over public Wi-Fi hotspots.
There are several reasons why IKEv2 can do this. For starters, it runs over UDP port 500, meaning it doesn’t use TCP connections. This allows it to work well with mobile devices that lack support for TCP.
Also, unlike other VPN protocols, IKEv2 does not require manual configuration. Instead, it automatically detects the presence of an active wireless network and connects to it. If you’re looking for something fast, reliable, and easy to configure, IKEv2 might be the answer.
In fact, according to our tests, IKEv2 is one of the fastest VPN protocols we’ve ever tested. It also happens to be one of the easiest to use. But what makes it stand out from the rest? Let’s find out.
What Is IKEv2 VPN Support?
IKEv2 stands for Internet Key Exchange version 2, one of the most secure protocols used to connect remote networks together over the Internet.
This protocol allows for encrypted communications between devices, and it’s considered much safer than older versions like IPSec. Unfortunately, many people don’t know about this protocol because VPN providers do not widely support it.
The good news is that more VPN services recognize how important IKEv2 is for mobile users and add support. So you’ll see more and better VPNs supporting IKEv2!
There are even some companies out there that specialize in providing IKEv2 connections exclusively.
List of the best IKEv2/IPsec VPNs to consider
When choosing a VPN protocol, there are many options to consider. But if you’re looking for a balance of security and speed, the IKEv2/IPsec protocol is a great choice.
IKEv2/IPsec is a VPN protocol that offers a high level of security while being fast and reliable. It’s perfect for users who want to browse the web securely and privately or for those who need to access blocked websites or content.
There are even some companies out there that specialize in providing IKEv2 connections exclusively.
There are many different IKEv2/IPsec VPNs available, so it’s important to choose one that’s right for you. To help you make the best decision, we’ve compiled a list of the best IKEv2/IPsec VPNs to consider.
ExpressVPN
ExpressVPN is a great option if you’re looking for a fast, reliable, and secure IKEv2/IPsec VPN.
It has servers in 94 countries, so you can always find a fast connection. And ExpressVPN uses strong encryption to protect your data from hackers and government surveillance.
Surfshark
Surfshark is a great option if you’re looking for an affordable IKEv2/IPsec VPN. It’s fast, reliable, and secure and has servers in 63 countries. Surfshark also offers a free trial, so you can try it before you buy it.
NordVPN
NordVPN is a great option if you’re looking for a powerful IKEv2/IPsec VPN. It has servers in 62 countries, so you can always find a fast connection.
NordVPN uses strong encryption to protect your data from hackers and government surveillance.
PrivateVPN
PrivateVPN is a great option if you’re looking for a fast, reliable, and secure IKEv2/IPsec VPN. It has servers in 60 countries, so you can always find a fast connection.
And PrivateVPN uses strong encryption to protect your data from hackers and government surveillance.
IPVanish
IPVanish is another great choice for an IKEv2 VPN. It’s a fast, reliable, and secure VPN that’s compatible with a wide range of devices.
IPVanish offers many features, including a kill switch, DNS leak protection, and a strict no-logs policy.
Private Internet Access
Private Internet Access: Private Internet Access is a great option if you’re looking for a low-cost IKEv2/IPSec VPN. It doesn’t have as many features as other options on this list, but it’s still a very solid VPN.
Hide.me
Hide.me is a great option if you’re looking for an IKEv2/IPSec VPN with a free option. It offers decent features, including AES-256 encryption and an automatic kill switch.
Many other great IKEv2/IPsec VPNs are available, but these are some of the best to consider. No matter which one you choose, you’ll be able to browse the web securely and privately.
Comparison of IKEv2 with other VPN Protocols Explained
We’ll be discussing IKEv2 in this section, but we’ll be referring to IPSec/IKEv2 because that’s the most common version of IPSec offered by VPN providers.
However, IKEv2 cannot usually be used alone because it was designed inside IPSec (which is why it’s paired up with IPSec).
Let’s look into how IKEv2 is compared with other VPN protocols.
Comparison between IKEv2 and L2TP/IPSec
L2TP/IPsec is one of the most common VPN protocols used today. While it offers a good balance of speed and security, it has some downsides. One downside is that it uses port 1723, which makes it easy to block with a simple firewall rule.
Another downside is that you often need to enable L2TP Passthru to make it work properly, which opens up the possibility of man-in-the-middle attacks.
There’s also the fact that L2TP/IPsec doesn’t encrypt traffic by default, making it possible for someone to intercept your data while it travels over the Internet.
IKEv2/IPSEC is another popular VPN protocol that works similarly to L2TP/IPSEC. Like L2TP/IPsec, IKEv2/IPsec also uses port 1723, but it encrypts traffic by default, meaning that anyone trying to snoop on your network traffic won’t be able to read it.
However, like L2TP/IPsec, IKEv3/IPsec is less secure than OpenVPN because it uses weaker encryption algorithms. In addition, IKEv2 requires manual configuration, which can be difficult if you want to set up multiple servers.
There are several different ways to implement IKEv2. Some vendors use proprietary code, whereas others use Open Source Software (OSS).
For example, Cisco Systems’ implementation of IKEv2 is called “Strongswan.” Strongswan supports AES 256-bit ciphers and SHA256 HMAC authentication.
On the other hand, OpenVPN implements IKEv2 via OpenSSL. OpenVPN supports AES 128-bit ciphers, SHA256 HMAC authentication, and Diffie Hellman Group 2 key exchange.
While many VPN providers support L2TP/IPSec and IKEv2/IPsec, it’s important to note that they aren’t always the best choice for every situation.
If you’re looking for a fast VPN connection, L2TP/IPSec might not provide enough security, while IKEv2/ISpc might be too slow.
Comparison between IKEv2 and IPSec
IKEv2 is just another name for IPsec and is part of the Internet Key Exchange (IKE), a network security protocol developed by the Internet Engineering Task Force (IETF).
IKE is designed to provide secure communications over public networks such as the Internet.
In addition, IKE supports multiple encryption algorithms, including strong encryption protocols like AES, 3DES, Blowfish, Twofish, Camellia, etc., and weak encryption protocols like DES, MD5, SHA1, SHA256, etc.
The main benefit of IKEv2 is that it allows for faster networking connections because it uses UDP rather than TCP.
However, there are some drawbacks to IKEv2. For one thing, IKEv2 does not support IPv6. Another disadvantage is that IKEv2 requires both ends of the connection to use the same version of IKE. If either end doesn’t do this, the connection fails.
Another problem with IKEv2 is that it is built into IPSec, making it difficult to upgrade or replace. This is why many people still prefer IPSec over IKEv2.
As far as performance goes, IKEv2 works about twice as fast as IPSec. And finally, IKEv2 can be implemented on most operating systems making it easier to implement than IPSec.
Comparison between IKEv2 and OpenVPN
OpenVPN is one of the most widely used VPN protocols, but how secure is it compared to IKEv2? We’ll compare both protocols side-by-side to find out.
The main reason why people choose OpenVPN over IKEv2 is because of its ease of use. You don’t have to set up anything special like certificates; you just connect to the server and start browsing. This is great for getting around firewalls and ensuring you’re safe from snooping eyes.
However, if you want to encrypt data at the IP level, IKEv2 offers better encryption than OpenVPN. Because OpenVPN works at the transport layer, it doesn’t encrypt the actual packets. Instead, it encrypts the connection between the client and the server. While this might sound good, it creates a lot of problems.
For example, if someone intercepts those encrypted packets, they won’t see anything useful about what’s happening on the Internet. If you want to hide your identity, you need to encrypt everything that goes across the wire. So, if you use OpenVPN, you’d have to do that yourself.
On the other hand, IKEv2 encrypts every single packet. This way, anyone sniffing the traffic couldn’t read it. You can safely browse without worrying about privacy issues if you’ve got a valid certificate installed.
Now, let’s talk about online speed. Both protocols are based on TCP/IP, so they shouldn’t differ too much here. When it comes to performance, OpenVPN wins hands down. It’s been tested to perform almost twice as fast as IKEv2. But if you want to keep things simple, stick with IKEv2. It’s easier to set up and configure, plus it’s free.
Comparison between IKEv2 and PPTP
PPTP is a protocol developed by Microsoft to provide VPN connections over Point-to-Point Tunneling Protocol (PPTP). This protocol allows you to connect to a remote server via a virtual private network (VPN), thus allowing you to access resources behind a firewall without exposing yourself to the outside world.
However, there are some drawbacks to PPTP. First off, it uses 128-bit encryption, which is considered weak today.
Secondly, it doesn’t allow for split tunneling, which means that all data packets go through the same route. Finally, PPTP is vulnerable to MITM attacks.
IKEv2 is a newer protocol designed to replace PPTP. It provides stronger security features such as 256-bit encryption, split tunneling, and authentication methods.
Furthermore, it supports IPv6 and IPSec protocols, which makes it compatible with most modern routers.
Comparison between IKEv2 and WireGuard®
WireGuard® is a relatively new technology that aims to replace IPSec and OpenVPN. It uses a custom crypto layer over TCP port 1812.
While it shares many similarities with VPN technologies like OpenVPN, it differs in design goals. For example, WireGuard doesn’t support NAT traversal.
IKEv2 is another very popular VPN protocol. Its main advantage is that it supports multiple encryption methods, including AES-256 and ChaCha20-Poly1305.
However, unlike WireGuard, IKEv2 requires the use of UDP rather than TCP. This makes it vulnerable to traffic analysis attacks.
Many VPN companies offer both solutions. If you’re looking for a secure VPN solution, consider choosing one based on security features. You’ll find plenty of information online about how each protocol works.
Comparison between IKEv2 and SoftEther
IKEv2 is an Internet Key Exchange version 2 protocol that uses UDP ports 500 and 4500. It’s widely used for remote access connections such as SSH tunnels, VNC Sessions, and RDP sessions. It’s also often used in combination with IPSec for VPN connectivity.
SoftEther is a free software implementation of the IKEv2 protocol. It provides both client and server functionality. This makes it perfect for creating tunneling applications, especially those that require an encrypted link between two hosts.
The most common use cases for IKEv2 include the following:
- Remote access via SSH
- Secure file transfer over HTTP
- Web browsing securely
- Remote administration
Comparison between IKEv2 and SSTP
IKEv2 and Secure Shell Tunneling Protocol (SSTP) are VPN protocols used to secure connections over public networks like the Internet.
They’re often confused because they look alike, but the two have some differences. Let’s take a closer look.
IKEv2 vs. Secure Shell Tunneling Protocol
IKEv2 and Secure SHell Tunneling Protocol (SSPT) provide encryption for data traveling across the Internet.
However, while IKEv2 is based on the IPsec protocol, SSTP is based on the SSH protocol. This difference leads to some important distinctions.
Security Levels
The main difference between IKEv2 and SSTP is the level of security offered. While IKEv2 offers strong encryption, SSTP provides less protection.
Because of this, IKEv2 is considered more secure than SSTP. When you use IKEv2, you’ll see a green lock icon next to the address bar in your browser. This indicates that your connection is protected with AES 256-bit encryption. You won’t see this symbol with SSTP.
Speed
One of the biggest advantages of IKEv2 is speed. With IKEv2, your traffic travels directly over IPSec tunnels. These tunnels ensure your data stays safe while passing through firewalls and proxy servers.
If you connect to a server via IKEv2, the packets travel directly from one computer to another without being routed through intermediate computers. This method is called “endpoint discovery.”
Unfortunately, this process takes longer than tunneling with SSTP. Because SSTP doesn’t require endpoint discovery, it’s generally slower than IKEv2.
Is the IKEv2 Protocol a Good for VPN?
IKEv2 is a protocol used to secure communications over IP networks. VPN providers are starting to offer it as an alternative to their existing protocols because it provides better security and performance. While there are many different versions of IKEv2, most are based on the original version developed by Cisco Systems. Here are three reasons why IKEv2 is becoming increasingly popular among VPN providers.
1. It Offers Better Security
The main benefit of using IKEv2 is that it offers much stronger encryption than older protocols like PPTP or L2TP/IPSec. This makes it harder for hackers to intercept traffic, even if they manage to break into your network.
2. It Provides More Reliable Performance
Because IKEv2 encrypts data packets, it requires less bandwidth than other protocols. If you’re trying to watch videos while traveling abroad, you’ll want to ensure that your connection isn’t dropping out frequently. With IKEv2, you won’t have to worry about that.
3. It Works Well with Mobile Devices
Many people now rely on smartphones and tablets to access the Internet. When you’re on the go, having reliable connections is essential. You don’t want to spend half of your trip waiting for a slow VPN server to load up.
Because IKEv2 uses UDP rather than TCP, it’s easier to set up and maintain. Plus, it doesn’t require additional software to work properly.
Conclusion
IKEv2 is a VPN and an encryption communication protocol used within the IPsec suite. It establishes a secure connection between a VPN client and a VPN server.
IKEv2 is a very safe way to connect to a VPN because it supports many strong encryption algorithms, and it also improved most of the security issues in the previous version, called IKEv1. IKEv2 has additional features like Mobile Mode, MOBIKE support, etc.
While it is a good option for mobile users, you shouldn’t forget about having a VPN provider that offers multiple protocols besides IKEv2.
We suggest choosing one that offers access to multiple VPN protocols, such as OpenVPN and Softether. You might also want to consider getting access to those protocols since they are really useful for desktop and laptop users.