FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
If your privacy and security are the prime concern, then using a well-protected Tor Browser will not let you down.
The common belief of Tor users, researchers, developers, and founders is that Internet users should have private access to uncensored websites.
The word “Tor” comes from the idea of “Onion routing.” The Tor network has thousands of relays, also known as Tor circuit, run by worldwide volunteers to keep Tor users safe.
When you use the Tor Browser, your online activity cannot be tracked by ISP, government agencies, or hackers.
What is Tor, and how it works?
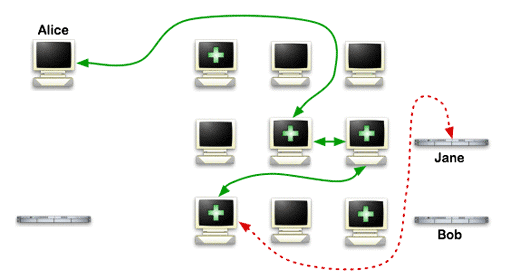
Tor is a computer network that is set up and run by thousands of volunteers worldwide.
Each computer in the network is known as a relay, is run by a software that creates interconnection on the internet. This network is also known as the Tor network.
Tor network is also known as a network of proxy servers that create an anonymous network connection. So that you can browse the web, send emails and instant messages anonymously.
The user client release data packets through three random Tor proxies called nodes.
The entry node work is to make connections with user client, data encryption, and forward to the next node.
The intermediate node work is to route traffic from entry nodes to output nodes.
The last, output nodes transmit data over the internet to reach website servers. Now, your output node IP address will be visible to the website administrator.
This way, you can achieve anonymity in the Tor network.
So, whenever you are connected to the Tor network, your activity is untraceable by ISP. The ISP cannot see the content of the traffic, not even which website you have visited.
The ISP can only see that you are connected to the Tor entry node, and the website administrator, on the other hand, can see the IP address of the exit node.
What to keep in Mind before Installing Tor Browser?
Before installing the Tor Browser, you need to make sure that you are downloading Tor Browser from the correct source.
You will find every detail on the Torproject.org download page. As per your device, you can download the Tor Browser installer.
Verify Tor Browser signature
Once you have download the installer, it is good to verify the Tor Browser signature.
Tor Browser’s signature signifies that downloaded installers are generated by developers, and it was not tampered by anyone else.
Each file in the installer package is accompanied by another file with the same name but with the different extension “.asc.” These .asc files are used to verify whether you have downloaded the correct installer file.
Further, to verify the signature, you have to install GnuPG software. For complete details on installation and verification of Tor Browser Installer, you can refer to this page.
How to Install the Tor Browser?
Once you have verified the Tor Browser signature, the next step is to install the Tor Browser.
Installing Tor Browser in Windows 10
Step 1: Here, we have taken an example of Windows 10. Mostly the procedure would be the same for other versions of Windows. So, to start the installation, you need to click on the EXE file.
Step 2: Like any other program, the installation process would be the same for the Tor Browser. But, there is a crucial difference you have to notice.
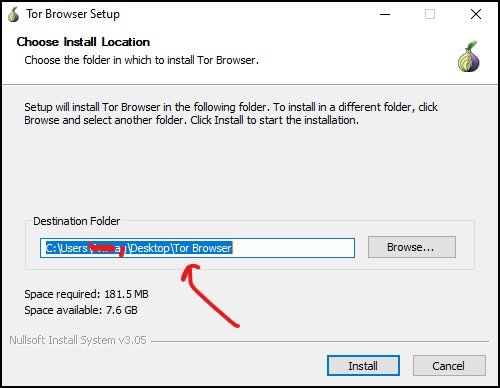
Unlike other programs or software, the default location is not the Program Files folder; instead, it has Desktop as a default location.
More importantly, the Tor Browser doesn’t integrate with Windows systems. So, you can choose independently any location like any Drive, document folder, or even you can select the external hard disk or USB drive.
After choosing a location, you can click on Install and rest it will take care of by Tor.
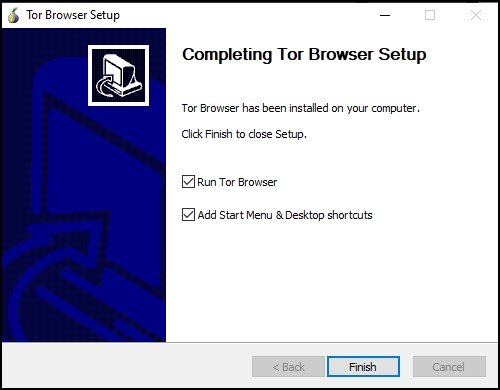
Step 3: After the installation has completed successfully, you can click on “Finish” to start Tor Browser.
Initially, when you are starting Tor Browser for the first time, it will put up two options – “Connect” and “Configure.”
Configuration in Tor Browser
The configuration part is simply the network setting, where they ask two things:
- Are you in a country where they censor Tor (such as Egypt, China, Turkey)
- Are you using a private network that required proxy
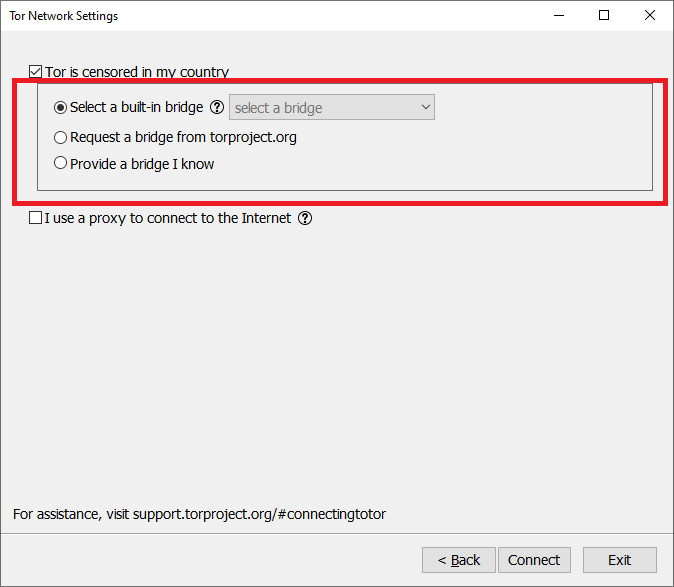
If you have checked the first option, “Tor is censored in my country,” then Tor Browser will take you through a series of configurations.
If you have opted for the option, it means that direct access to the Tor network is blocked. So, getting around these blocks, Tor Browser has included “circumvention tools.”
These tools are also called “pluggable transports,” and to get complete details on circumvention tools, you can click here.
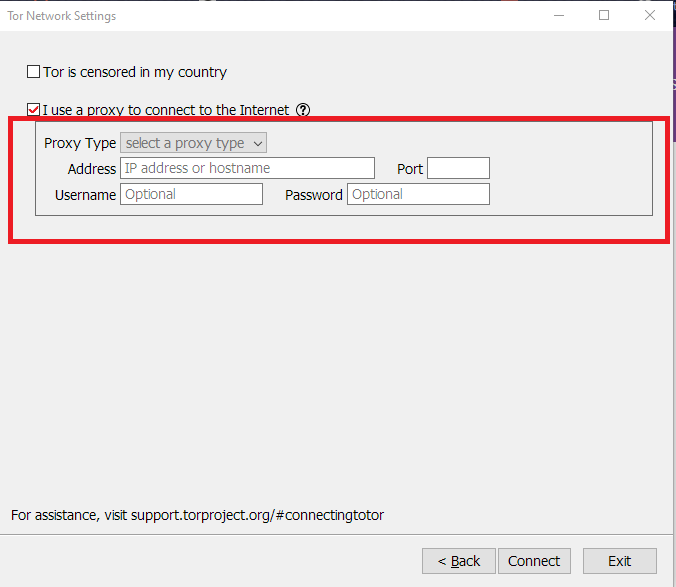
The second checkbox option is “I use a proxy to connect to the Internet.” In most cases, this option is not necessary. But, if the network uses a proxy, then it should also get configured with the Tor browser.
If you know the proxies, then you can easily put it in the configuration part like Proxy type, IP address, Username, and Password. Otherwise, take the help of a network administrator for further configuration.
If you don’t fall on any of these options, then simply click on “Connect” to start connecting with the Tor network.
Step 4: Initially, while establishing a connection, it will take some time, and then it will greet you with a welcome screen.
You can even look for starting tutorials by clicking on the “New to Tor Browser Let’s get started” on the top left side of the screen.
How to browse anonymously in Tor Browser?
The default search engine for Tor Browser is DuckDuckGo.com, which is primarily a safe search engine that protects the privacy of the users and doesn’t track online activity.
Why use Tor Browser?
When you connect to any websites, it not only the administrator of the sites that can track your activity but also by third party services.
The third-party services use different analytics trackers that can link your online activity from one site to another site. This way, they can analyze your online behavior and pattern.
But, with Tor Browser, website administrator, or any third party services cannot discover your exact location and IP address, not even they can analyze your online behavior.
How Tor Browser protect your identity?
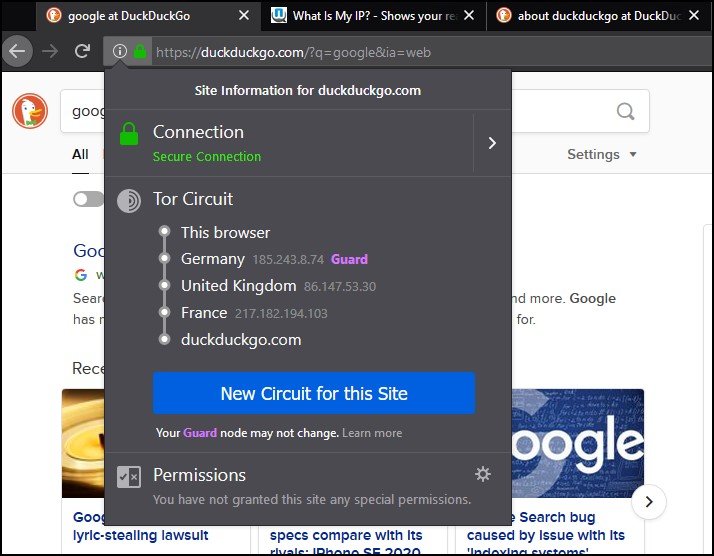
Tor Browser uses Tor Circuit to protect your identity. You will get detail of the Tor Circuit by clicking on the information icon on the left side of the address bar.
So, for every site, they use different tor Circuit, which makes it difficult for third-party services to track your activity. They cannot identify whether the two different sites are originated from the same browser.
But, the Tor Circuit for the single site doesn’t change when you visit different pages of the same website.
In the Tor Circuit, the first node is known as an entry node or Guard node, which remains unchanged for 2-3 months. But, the other node change with the different domain names.
How to adjust your identity information with different sites?
We know that Tor Browser protects your anonymity on the web, but some sites still require some of your information.
Social networking sites or email accounts require information like usernames, passwords, or any other identity information. So, to reveal such information, you need to adjust the Tor Browser.
The Tor Browser is also helpful to log in to a site that was censored in your network.
How to change Identity and Tor Circuits in Tor Browser?
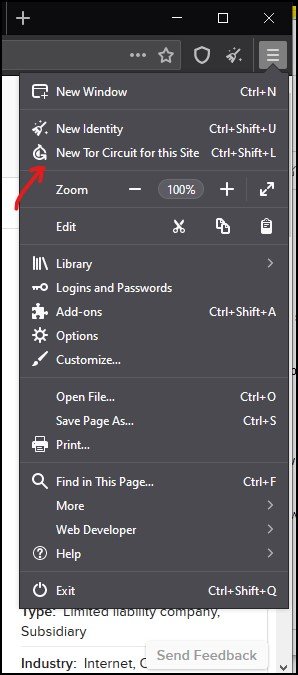
To change your identity and Tor Circuit, Tor Browser provides you with two options.
- New Identity
- New Tor Circuit for this site
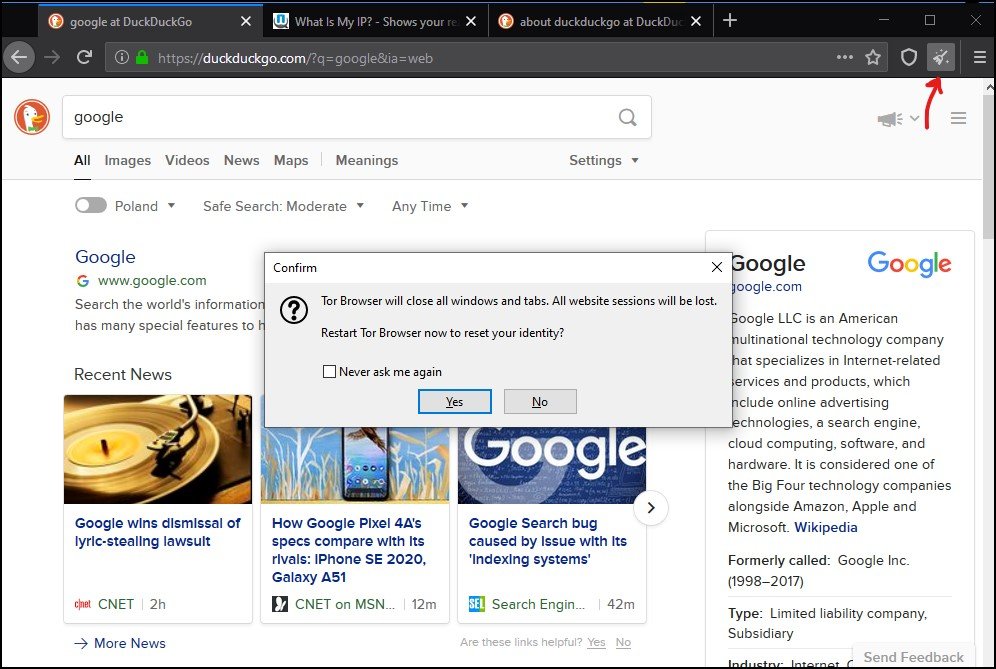
The “New Identity” option clears your current identity and Tor Circuit with the visiting sites. It will clear cookies and browsing history and start a new Tor Circuit for the visiting sites.
You can reach the “New Identity” function from the broomstick icon on the right side of the address bar.
But, if you like to change the current active Tor Circuit of the currently active tab or window, then the “New Tor Circuit for this site” option will be helpful.
This option will not clear any of your private information or unlink your current activity with the site. You can access this option by clicking on the site information menu in the URL bar.
This option is also useful when you are not able to connect to a present site, or it is not loading correctly.
How to adjust the security settings of the Tor Browser?
Tor Browser, by default, protects your security by encrypting your browsing data. You can further increase your security level by disabling some of the web features.
But disabling web features may affect the experience with some of the websites. In some cases, it may stop web pages from functioning correctly.
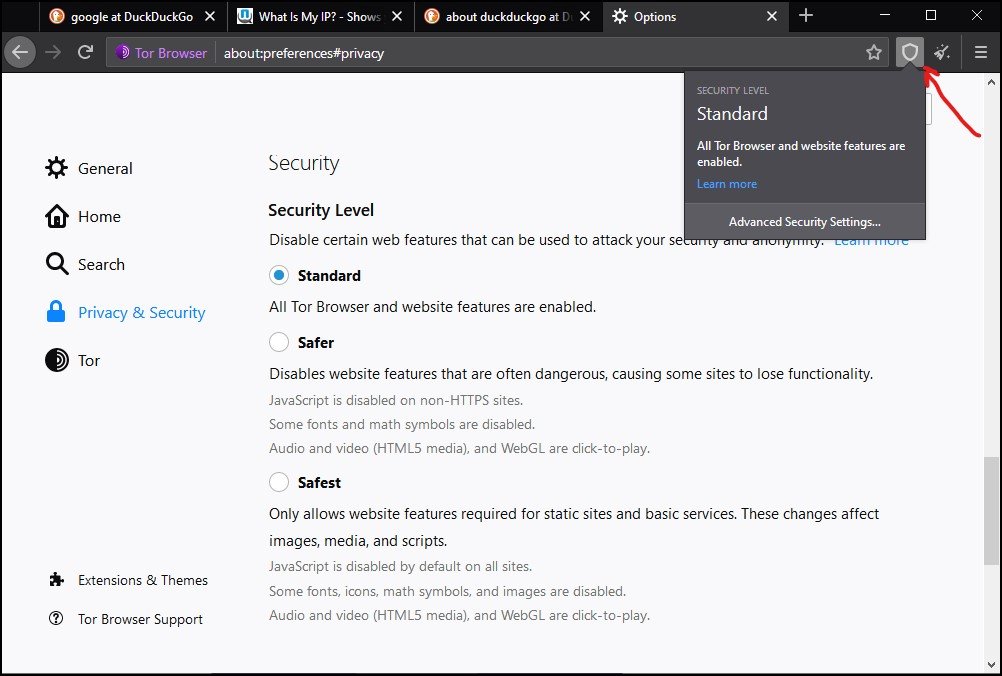
You can access security features by clicking on the shield icon on the right-hand side of the Tor Browser web URL. Further, you need to click on “Advanced Security Setting” to adjust security settings.
Security level in Tor Browser
The security in Tor Browser is categorized under three heads:
- Standard
- Safer
- Safest
By default, the Tor Browser is set on the Standard level, where all Tor Browser and websites are enabled.
In the Safer level, JavaScript is disabled on all non-HTTPS sites. They also disable some of the fonts and math symbols. Even the audio and video in HTML5 media and WebGL are not allowed to play.
In the Safest level, JavaScript is disabled in all sites; additionally, it carries all the features of the Safer level.
Moreover, by default, the flash player in Tor Browser is disabled, and enabling this feature is not recommended because it may reveal your real IP address.
Further, JavaScript may enhance web experience by offering certain interactive elements such as video, animation, audio. But, it may interfere with the security of the browser leading to deanonymization.
Also, to stay safe, Tor Browser does not recommend any additional add-ons or plugins because it may compromise your privacy.
If you like to know more details on Tor Browser security features, then click on three bars on the top right corner of the browser and then click on “Option” in Windows and “Preferences” in Mac.
Next, go to the “Privacy & Security” menu and then go to the History section to adjust your private browsing mode. Further, in the “Browser Privacy” section, you can adjust the “Cookies and Site Data” setting.
Is Tor Browser and VPN is same?
Both the Tor Browser and VPN protect your identity and security online. But they are not the same.
VPN protects your identity and security by providing end-to-end encryption through a secure channel to a remote server and then to a website.
Tor Browser protects your identity and security till the exit node; after that, encryption is removed for non-HTTPS sites. It means that it is possible to spy your activity from the exit node for unsecured HTTP sites.
Which one is better? VPN vs. Tor Browser
There is no doubt that both VPN and Tor Browser provide privacy and security to web users. But, when we compare both VPN and Tor Browser, then VPN offers complete security and confidentiality.
Tor Browser is not entirely secure because the system has some weaknesses, especially with HTTP sites.
Moreover, the Tor Browser is not the best choice for streaming and downloading videos.
Also, Tor Browser discourages the use of torrent, which means that torrent traffic is not protected, and it may expose your real IP address.
If you are looking for streaming or torrent, then VPN is much better protection. You can use the most popular and best VPN like NordVPN, Express VPN, and SurfSark.
Overall, the NordVPN is a complete VPN with all the features and security that may enhance your web experience.
You can also use both VPN and Tor Browser together that will maximize security and privacy.
If you like to use Tor Browser with VPN, then you can follow this guide.