FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
In an insecure network such as the Internet, we require security to access sensitive information and resources from remote computers.
Secure Socket Shell or Secure Shell (SSH), a network protocol, was introduced to facilitate safe and secure access remotely.
What is SSH?
The Secure Shell is a network protocol that provides solid encrypted communication between the user and remote computer.
Further, SSH is an application layer protocol that is in the 7th layer of the OSI model.
Moreover, the Secure Shell provides two types of security; one is password-based, and the other is key-based authentication.
Password-based authentication requires a username and password to access the remote server. In contrast, key-based authentication is a cryptographically secure key pair.
The cryptographically secure key pair follows an encryption scheme that uses one public and private key.
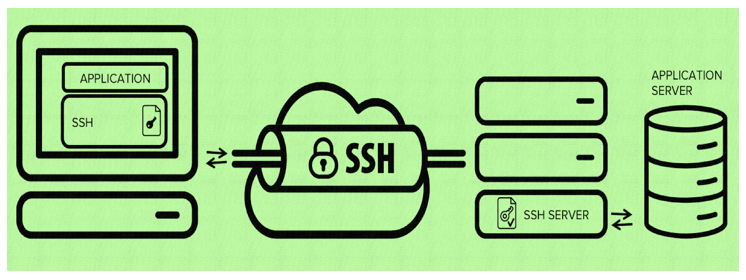
Also, the SSH technology is based on a client-server network model that creates a pathway to access a remote computer or server.
How does Secure Shell Architecture work?
As we have discussed, the Secure Shell or SSH architecture is based on a client-server network model.
You can establish a connection between client and server by installing client program in the client system and server program in the server system.
Also, the server requires default HTTP port 22 to establish a connection.
Where to use Secure Shell or SSH?
The Secure Shell application comes as default in almost all operating systems.
You can use Secure Shell (SSH) for a variety of purposes which includes:
- Logging and establishing communication between the local computer and remote computers or servers to provide support and maintenance.
- Access and transfer of files or resources between the local computer and remote server.
- You can execute commands on remote computers or servers.
- Remotely perform administration tasks that offer support and updates.
- SSH can be used to create a secure shell tunnel that enables application protocols to redirect traffics to a particular IP address or port.
How to use Secure Shell or SSH?
The SSH command is the most common way to use Secure Shell or SSH to access a remote computer.
Some of the most used commands are:
ssh – It is used to login and execute commands on the remote computer
sshd – It is a daemon program that provides a secure communication network by authorizing the incoming request of the client to get access to server localhost.
ssh-keygen – It is a command used to generate new authentication key pairs for SSH. Further, the key pairs are used for automatic logins, authenticating hosts, and single sign-on.
ssh-copy-id – It is an SSH command used to install an SSH authorization key on a server. The primary purpose is to provide access without requiring a password for login.
sftp – It stands for Secure File Transfer Protocol (SFTP), a network protocol for accessing, transferring, and managing files on remote servers or computers.
scp – It stands for Secure Copy Protocol. SSCP is used to transfer files securely at a much higher speed compared to SFTP. Unlike SFTP, it cannot list remote directories and delete the remote file.
Now, we will look after different activities you can implement using SSH commands.
Access remote server
The SSH command used to access the remote server is
ssh user1@server1.xyzdomain.com
Here, user1 is the server user, which represents the account you want to access.
And, server1.xyzdomain.com is the server address of the computer you want to access.
Besides, you can also use an IP address instead of DNS or nameserver.
For example, ssh user1@10.10.1.3
After you have typed the above command and hit enter, it will prompt you to enter a password.
If you have entered the correct password, it will greet you with a remote terminal window; else, it will show nothing.
Creating key pair
You can create new public and private key pairs for authentication of remote servers or computers.
ssh-keygen -t rsa
The above command generates public-private RSA key pair. in RSA encryption, encryption is public, but the decryption is private.
Transferring or copying file
You can use the SSH command to copy files from one computer to another computer.
scp <em>filename1</em> <em>username@remotehost1:destinationPath</em>
Here, filename1 is the file that is to be copied to the remote computer current directory. And, the remaining part represents the server and user details and the destination path to the remote computer.