FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
Are you worried about online privacy and security?
Wondering whether your online activity like visiting a site, clicking on links, and download files would be tracked by hackers, government agencies, or companies?
There are so many online activities you can do without getting snooped, and for that, you need a proxy.
A proxy is an intermediary server between you and the rest of the internet.
Usually, when you visit any website, you are directly getting in contact with the website server. But, when you are using a proxy, then the proxy will communicate to the website server on your behalf.
Without a proxy, web scraping is impossible. Also, you cannot protect your online identity and data leaks without a proxy.
So, the proxy is a powerful tool that can be used in both personal and business cases alike.
But, how to define a proxy in detail? How does proxy work? And, what are the type of proxy and their differences?
What happens when you browse the internet?
Before getting connected to the internet, every computer or device is assigned an Internet Protocol (IP address). This IP address is the primary source of communication, which is given by your ISPs with the rest of the online resources.
So, whenever you request any online resources or visit any websites, your activity is tracked by ISP as well as a website administrator.
They can identify how many times you have visited that website, how long you spend on a particular site, which links and files you have downloaded, and what is your present location.
Technically, they can scrap more information about your online activity, than you have ever thought of.
Nowadays, your online activity and personal data is a source of money for most companies. They use and manipulate gathered online data in both positive and negative ways.
But, to most people, trade-offs of personal data are unacceptable, and they need online privacy.
Luckily, there are ways to stop getting tracked by your ISPs or website administrator. And, one of the easy ways is by using a proxy, also known as a proxy server.
What is a proxy?
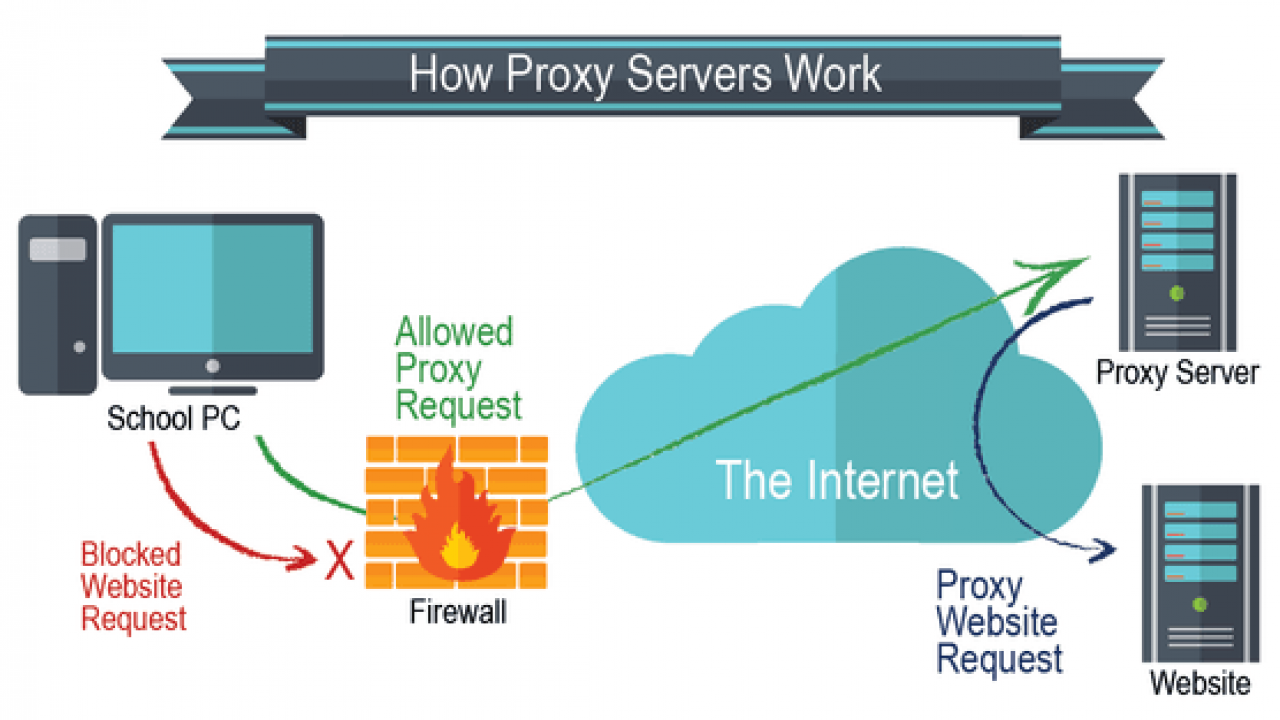
A proxy acts as an intermediary or gateway between web users like you and the rest of the internet or online resources.
When you start using a proxy, your browser will first connect with a proxy server, and the proxy server receives your request and send it to the website server. That’s why the proxy server is also known as “forward proxy.”
Subsequently, the website server responds to the proxy server and, the proxy server collects the response and sends it back to you.
Here, the proxy server is referred to as someone who is being authorized to take action on your behalf.
Instead of web users communicating directly to the website, the proxy server will handle the relationship on your behalf.
How does a proxy server work?
An internet device or software typically falls under two roles; clients and servers. Clients always request data or information from a server.
As a web user, your browser works as a client, which requests data or information from a server. So, whenever you request any websites from your browser, the servers accept requests and reply with requested data.
Behind any website, there can be a server or group of servers that work to deliver your requested website. These requests and replies, which are generated from a client and communicated by servers, is known as traffic.
So, without a proxy, your browser directly communicates with website servers. This whole communication between your browser and the website server is publicly available to track by your ISP or website administrator.
But, if you want to secure any type of communication that is exposed to the public, then you have to use a proxy.
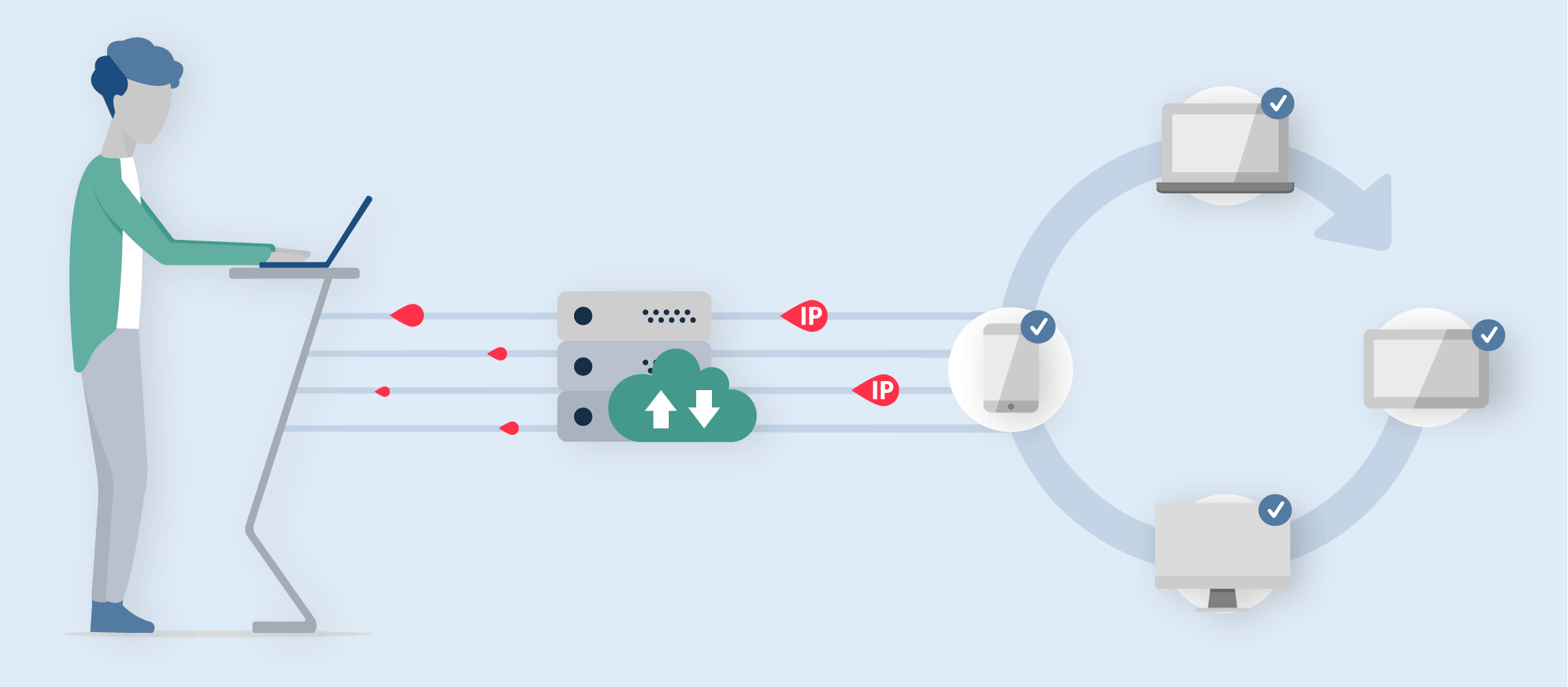
A proxy server works as an intermediary server between web users and web servers, and it can handle all traffic and communication on your behalf.
A proxy server is another computer, which has its IP address and is connected to both clients and the rest of the internet.
So, you, as a web user, only communicate with the proxy. And, proxy will forward your request to the internet on your behalf. In return, any replies received by proxy from the internet will send it to your computer.
Below, you will be introduced to different types of proxy, and every kind of proxy has a different role to play. Some proxies may conceal your device IP address, and some kind of proxy is powerful enough to encrypt your communication data.
Benefits and usage of the proxy server
The proxy servers can be used for different purposes and have many advantages which include:
- Maintaining privacy by concealing your IP address while browsing
- Keep you secure in a private network like a corporate network
- Help you to bypass content filters
- Help you to browse geographically restricted content and local pages of other countries
- It will save bandwidth and increase website performance through caching
- Help in web scraping and scraping search engine queries without getting blocked
- You can run as many software like keyword tracking software without getting blocked
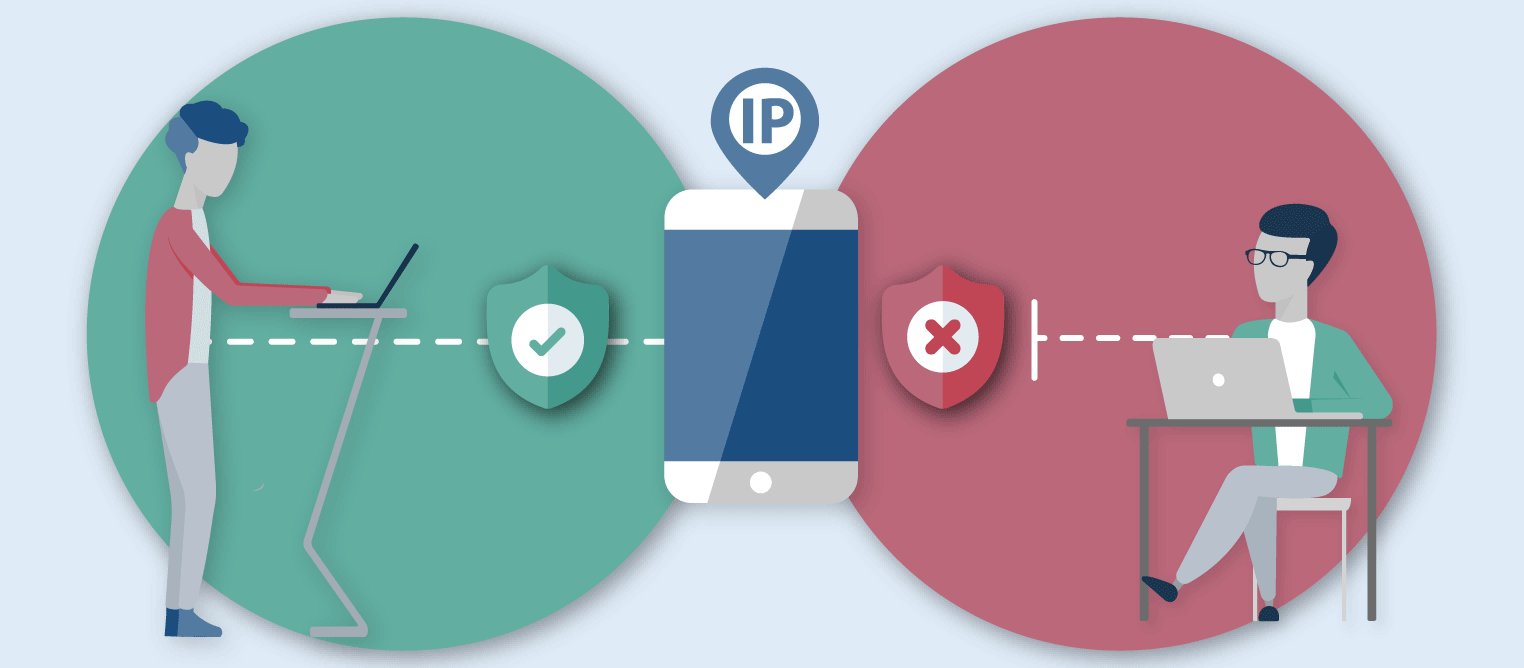
Do all proxy hide your IP address?
Well, it depends on which type of proxy you are using.
In schools, colleges, or organizations, the proxy is used only for web filtering and security purpose. So, whenever you request any website, they pass your real IP address and geographical location to the requested servers.
But, most types of proxy hides your IP address and exact location. Again, it depends upon the level of anonymity a particular proxy is using.
Moreover, other than hiding your original IP address, the proxy has plenty of other primary goals to achieve, such as scraping web content, encrypting communication, and bypassing geo-blocks.
Does a proxy provide anonymity?
Well, again, it depends upon which type of proxy you are using. Because not all proxies are created equal, and you have to choose from the various levels of anonymity.
Undoubtedly, online privacy is the prime concern for most of the web users. They don’t like to get tracked by ISPs and government agencies and fall in the prying eyes of cybercriminals.
The IP address is one of the most common ways to trace your online activity, such as an appropriate location, which websites you have visited, and how much time you have spent on those websites.
However, the other way to track your online activity is through the stored cookies. By using cookies, the marketer can trace your online behavior and pattern.
Thankfully, the use of proxy will provide you with various levels of anonymity and web privacy. So, it would be difficult for government agencies or ISPs to keep tabs on your online activity.
You can level-up your anonymity by hiding your IP address and utilizing end-to-end encryption of traffic.
Type of Proxy Server
The type of proxy servers in term of their IP origin
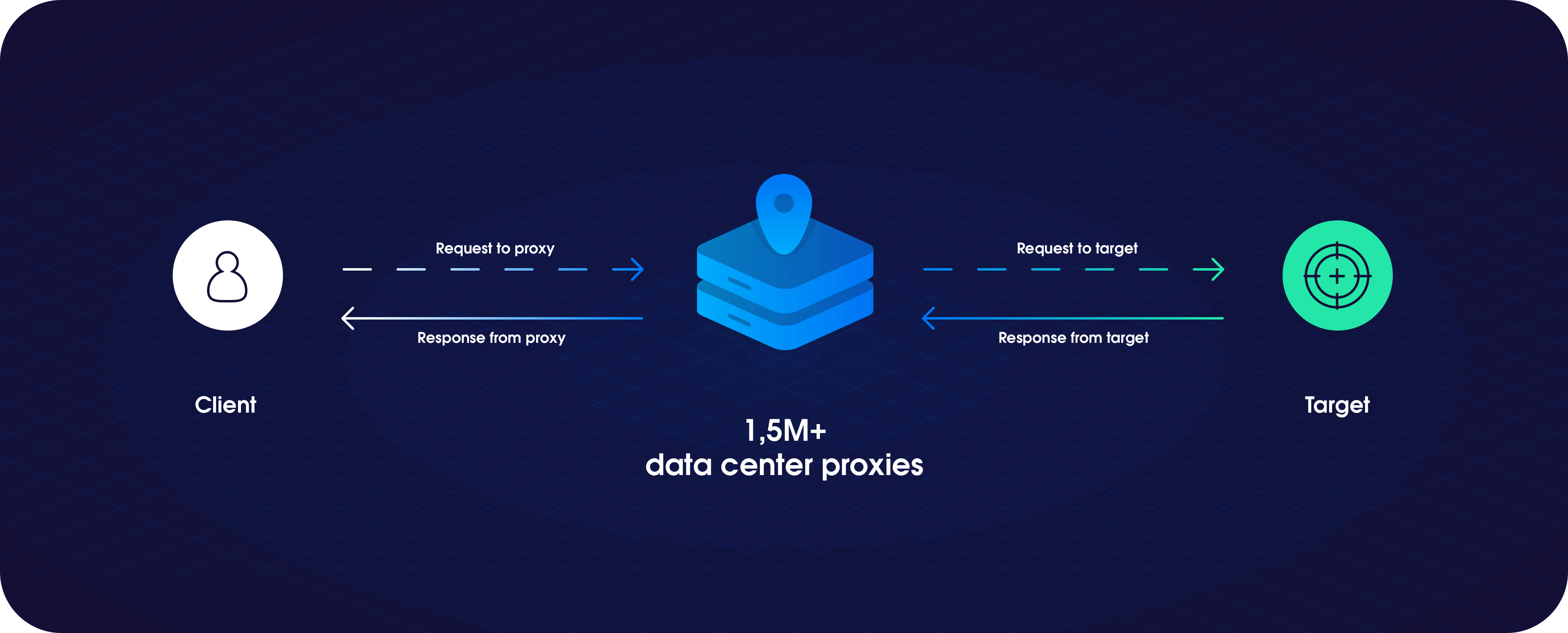
The main type of proxy servers in terms of their IP origin are residential proxy and datacenter proxy.
Residential Proxy
Residential proxies are by far the best proxy server for most uses because it has a real IP address provided by a real ISP to a homeowner.
Additionally, because of real IP addresses, it is detected as an actual physical location from where you can imitate as a real organic web user.
Further, residential proxy will appear to all web servers as real web users, which is impossible to detect.
The residential proxy is very much helpful in getting access to essential data and documents because it removes any type of geographical restriction or cloaking.
Datacenter proxy
Datacenter proxies are not affiliated with real ISP, but it imitates a real internet connection. It has a non-physical IP address that is artificially created in datacenters.
Additionally, you will find that a single server can host hundreds of datacenter proxies, but all datacenter proxies share the same server’s IP subnetwork.
That’s why all groups of datacenter proxy will look very similar and are more prone to cloaking or ban.
Although the data center proxy provides complete private IP authentication and anonymity. But, when it was compared to the residential proxy, the datacenters proxy has much higher speed and cheap to purchase.
The type of proxy in term of their anonymity level
Transparent Proxy
Transparent proxy, also known as intercepting proxy, doesn’t provide any type of privacy or security to your connection. It passes real IP address and location to the web servers.
The web servers can easily detect that you are connected with proxy.
Moreover, the transparent proxy is used for content filtering and caching purposes. It is not all preferred for any type of security and privacy purposes.
A transparent proxy is also known as intercepting proxy, inline proxy, or forced proxy.
You will find a transparent proxy in school, colleges, and corporate, where they use a transparent proxy for web filtering and caching of websites.
Anonymous Proxy
The anonymous proxy doesn’t forward your real IP address and location detail to the webserver.
Instead of real IP address, the website server will receive a fake IP address, that’s why anonymous proxies are sometimes known as distorting proxies.
However, similar to a transparent proxy, the anonymous proxy is traceable by a web server that you are using as a proxy server.
It may also be possible that some websites deny service to proxy servers. So, with anonymous proxy, you can’t be able to visit some of these websites.
It gives a bit of online privacy to web users, but complete protection of your identity is not possible.
An anonymous proxy is used at a low level of web content scraping, but it is not recommended for the majority of online purposes.
Elite Proxy or High anonymity proxy
Elite proxy, also known as high anonymity proxy, provides full anonymity to the web users. The proxy servers modify the HTTP header to remove any of your information altogether.
So, the website server won’t be able to detect that you are using proxy servers.
Also, the high anonymity proxy adds the extra layer of protection by periodically changing the IP address, which makes it very difficult to snoop.
The high anonymity proxies are mostly preferred by sneakers or scraping bots. So, their web servers are unable to detect that you are using proxies and thus protect your IP getting banned.
High anonymity proxy also encourages fraudsters to engage in fraudulent behavior, which is illegal.
Type of Proxy Server based on Protocol
HTTP proxy
HTTP proxy act as a tunnel that routes HTTP request from web browser to the internet. For multiple purposes such as security, an HTTP proxy can serve as both an HTTP client and an HTTP server.
Its primary purposes lie in providing caching to web pages that make them load faster. Currently, most of the browsers utilize HTTP proxy for caching web pages so that frequently visited websites can be accessed more quickly.
So, whenever you visit any websites, HTTP proxy will first try to search the site in the cache. If the website is already there, then it will get downloaded, else it will request from the website server.
Additionally, HTTP proxy is utilized in web filtering and in reformatting web pages to suit your devices better.
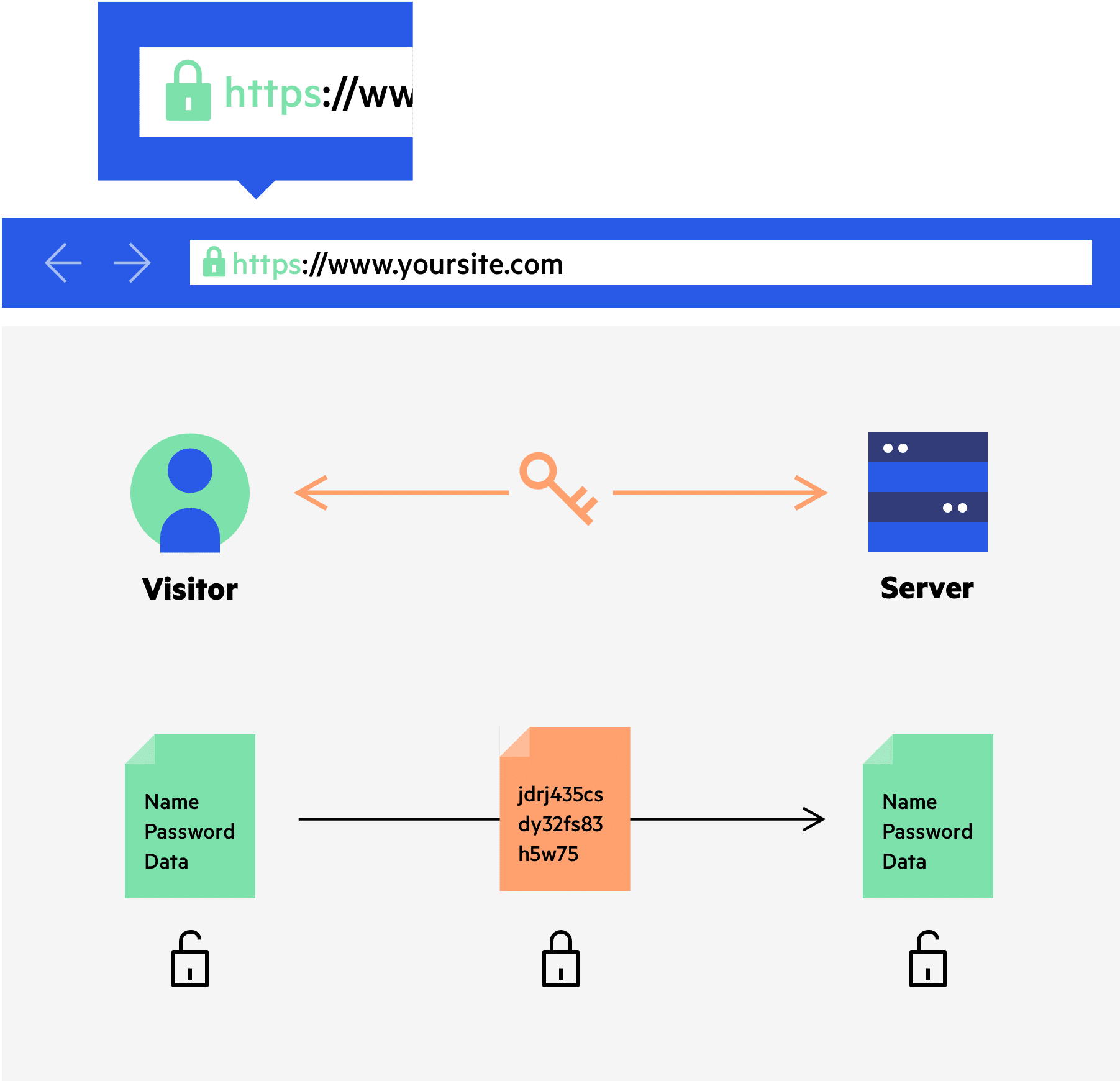
HTTPS proxy or SSL proxy
HTTPS proxy, also known as SSL proxy, is a Secure Sockets Layer protocol that protects your data during transmission from web users to web servers.
It acts as an additional security layer that provides end to end encryption to protect from eavesdropping during transmission of data.
It establishes a secure connection between both client and web server side to stay safe from any type of transaction or logging to a website.
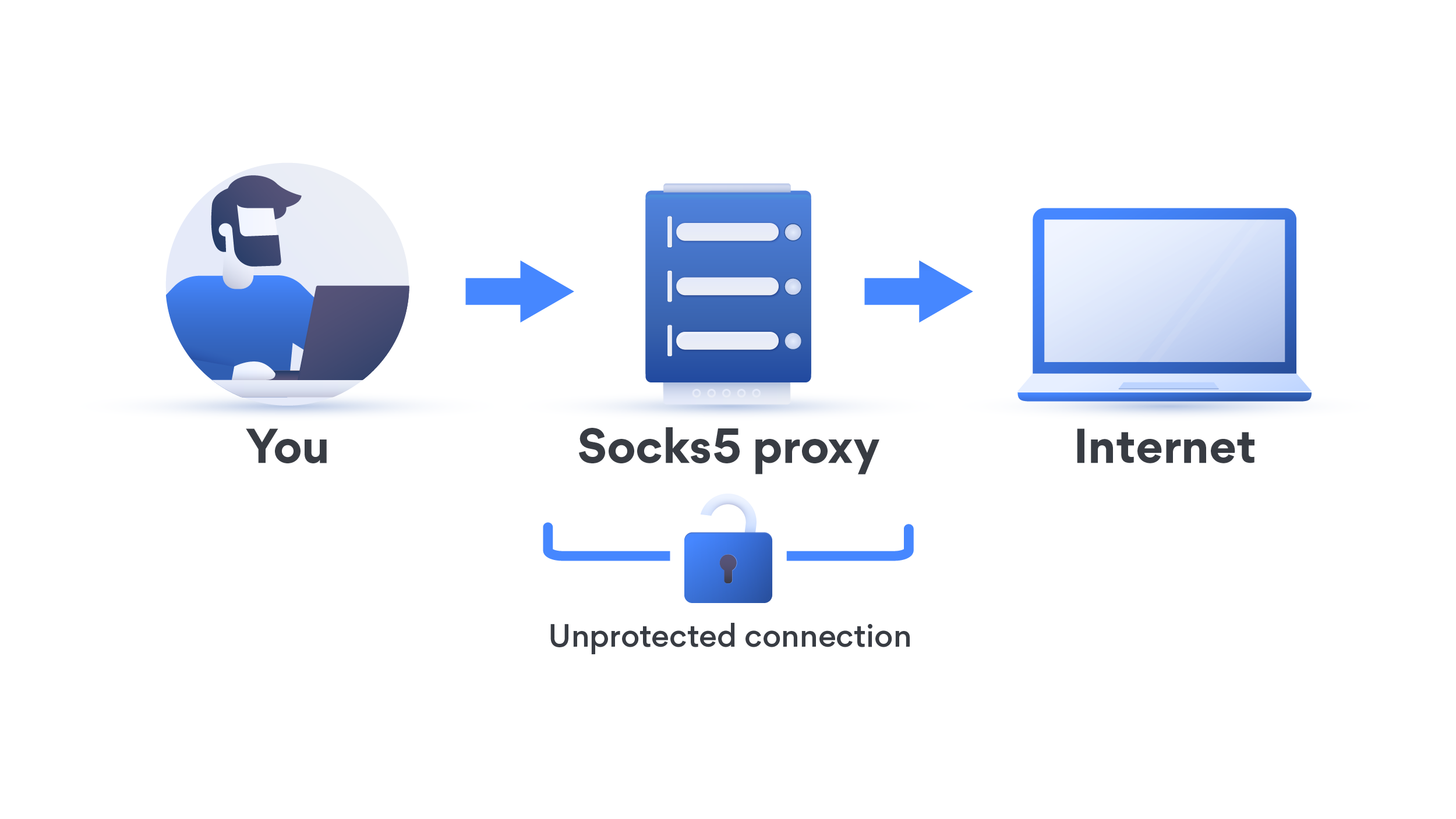
SOCKS proxy
The SOCKS proxy is considered as the most secure and advanced proxy type. It provides security to various types of traffic generated by protocols like HTTP, HTTPS, SMTP, and FTP.
It establishes a connection with servers behind a firewall and route traffic generated by any protocol or program.
For the exchange of packets between clients and servers, it creates TCP (transmission control protocol) connection behind the firewall on behalf of clients.
Additionally, if clients are connected with SOCKS proxy, then they are not permitted to establish TCP connection with any servers. So, if they want, they have to go through the SOCKS proxy.
If we go deeper, then we will find that SOCKS proxy sits at layer 5 of the Open Systems Interconnection (OSI) model.
It further means that it lies in between SSL (layer 7) and TCP/IP (layer 4) of the OSI model, which can handle any type of traffic requests such as HTTP, HTTPS, SMTP, POP3, and FTP.
Subsequently, SOCKS proxy can be used for any network tasks such as web browsing, peer-to-peer connection, file transfer, email, VoIP or video calls, and much more.
Compare to SOCKS proxy, HTTP and HTTPS proxy can interpret and forward requests from the client to the server and are often referred to as application proxies.
There are two versions of SOCKS proxy – SOCKS4 and SOCKS5 proxy.
The SOCKS5 proxy is more advanced, secure, and supports authentication. Whereas, SOCKS4 proxy doesn’t support authentication.
FTP proxy
FTP proxy is termed as File Transfer Protocol, which can be used in different applications for uploading data to a web server.
The most common usage of FTP proxy is in building a website. To make your website accessible on the internet, you need to upload your site to a web server.
To create a connection with a web server, you have to use the FTP application, also known as FTP client. So, to make the FTP connection more secure and advance, the FTP proxy server is useful.
FTP proxy servers make the transmission of data more secure and safe from hackers. It will keep track of FTP traffic and ensure that relaying traffic is in a safe environment.
Type of proxies based on access
Private proxy
Private proxy is the most used proxy because it is a cheap proxy compared to a dedicated proxy. The word “Private” does not mean that it deals with privacy; instead, it highlights product features.
In most cases, the private proxy means it requires authentication as opposed to the public proxy. It also means that a single client can use a private proxy at the same time.
Most web users get confused between the private proxy and dedicated proxy. Multiple users can use the private proxy, but the dedicated proxy is devoted only to a single client.
Dedicated proxy
A dedicated proxy is not shared, which means only a single user can use it with proper authentication.
It is used by users who are interested in web scraping or bot applications like Twitter bot and Instagram bot.
The other benefit of a dedicated proxy is that it won’t get blocked or burn out due to overuse.
Shared proxy
Shared proxy are those proxies that can be shared with multiple users but with limitations at the same time.
It is also one of the cheapest proxies in the market. Moreover, shared proxy quickly gets burn out or blocked due to overuse. So, on heavy usage, a shared proxy is not recommended.
The shared proxy needs robust network architecture to facilitate multiple shared proxy connections at the same time. Otherwise, the web user will face deficient speed and latency.
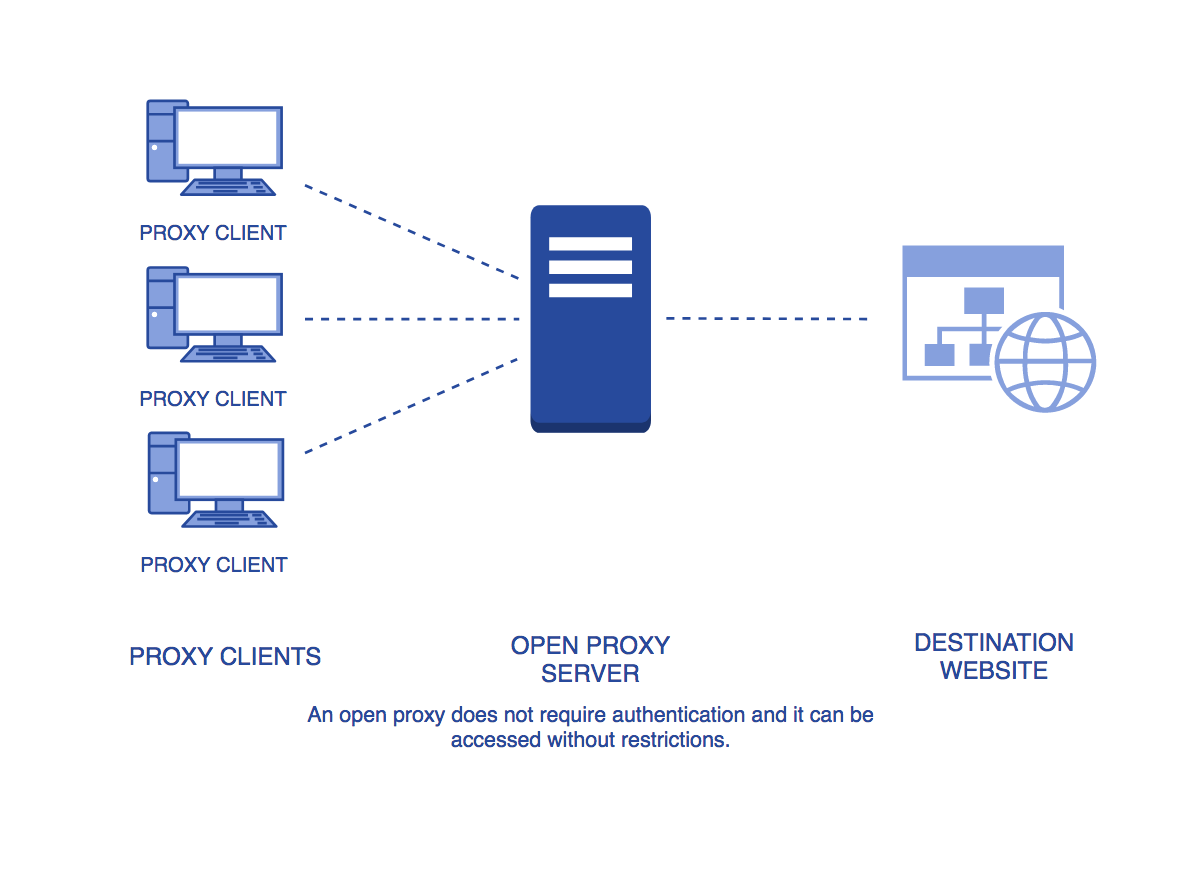
Public proxy
Public proxy, also known as an open proxy, is readily available to anyone, but it is unreliable, insecure, and unsafe proxies. Through the public proxy, hackers can easily track your online activity and can steal your data.
Further, the use of a public proxy can also be more prone to abuse and malware infections. Moreover, most of the open proxy gets quickly burn out within a minute.
Thus, gathering public proxies from millions of open proxy is an unscalable approach.
Type of proxy based on the duration
Non rotating or static IP proxy
Non rotating or static IP proxy are originated and provided by Datacenter proxy.
The datacenter proxy providers charge for the given number of proxies in a package. For additional proxy, you have to pay more or look for different packages.
This type of proxy is used in most of the application or add-ons. And, if the proxy gets burn out or blocked, the providers may offer a replacement.
Otherwise, for one month or more, you have to stick with given proxies.
Rotating proxy or Back-connect proxy
Rotating proxy, also known as Back-connect proxy, change automatically after a particular period and get replaced with new ones.
So, the rotating proxy provides better anonymity and speed compared to non-rotating or static IP proxy.
It is used mostly in heavy web scraping and a large number of bot applications. Currently, the rotating proxy is provided by a residential proxy, which contains a large number of proxy for rotation.
Additionally, the pool of proxies in a rotating proxy server does not share any subnetwork; otherwise, it would be useless.
Moreover, Datacenter proxy servers are still experimenting on how to generate the rotating proxy.
Type of proxy based on a modification of data
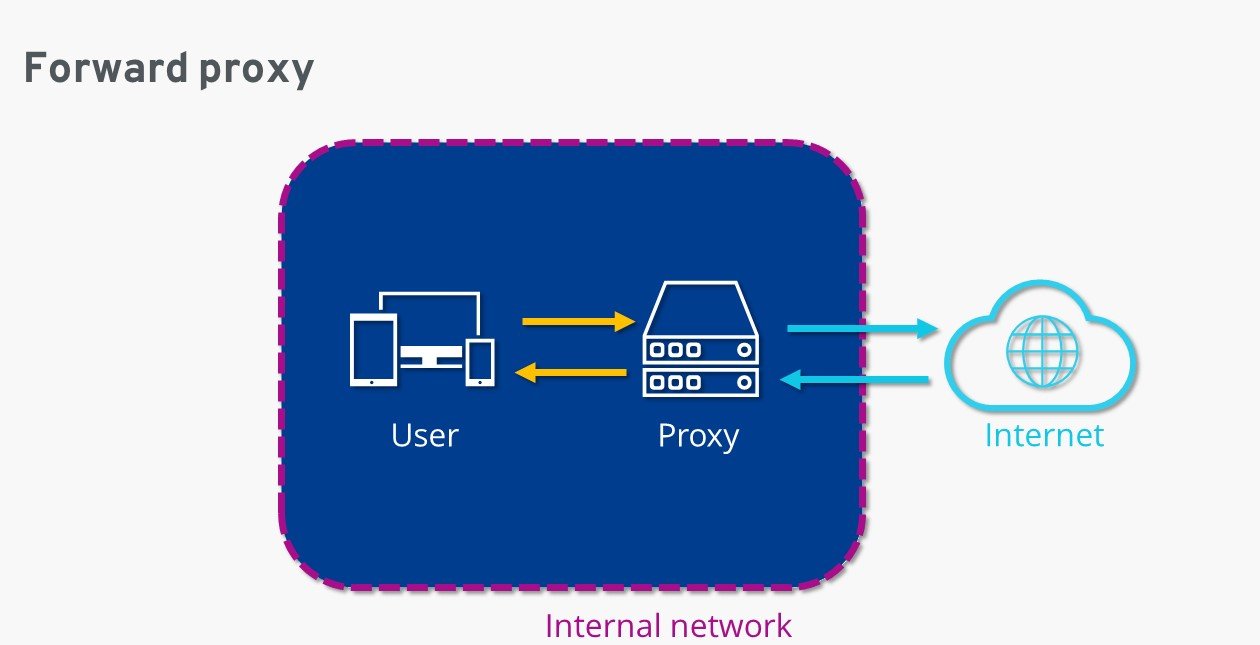
Forward proxy
Forward proxy servers are a general proxy that is used by the web client to access web servers.
The main work of the forward proxy server is to take the request from the client and forward it to the webserver.
After the web server has processed the request, the web server forwards the response to the proxy server, and then the proxy server forwards it to the client.
All proxy types which we have discussed above are forward proxy, which is originated from the web client.
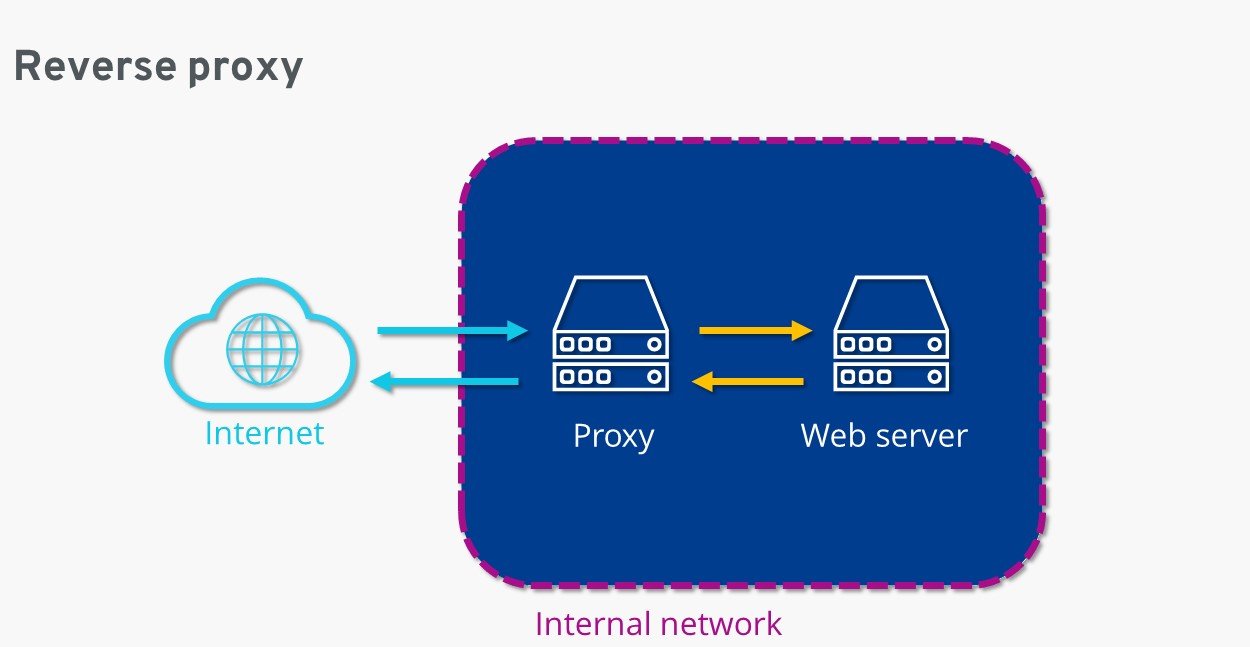
Reverse proxy
A reverse proxy resides on the webserver side as opposed to the web client.
Its primary purpose is to keep the web server safe and secure from incoming traffic. It also uses authentication and decryption techniques for all incoming traffic.
Further, the reverse proxy uses a caching technique to deliver content faster. Additionally, it also distributes the traffic to different servers to balance the load.
What is the difference between proxy and VPN?
The proxy and VPN are both used to keep your online activity secrets and secure, such as browsing the internet, downloading files, streaming videos, and sending emails.
But, both the tools differ in functionality and accessibility.
Proxy has limitations, which means it can be used with limited apps or browsers depending upon access type.
But, when using VPN on our system, it will let you access all type of apps and browsers belongs to that system with no restriction.
As per functionality, VPN differs with proxy in many ways.
Encrypt your information
Encryption is always included with a VPN that keeps your browsing activity or sending and receiving data safe and secure from government agencies and hackers.
But, all proxy are secure and encrypted like the HTTPS and the SOCKS proxy is safe and reliable, but HTTP proxy is not secure.
Promote online privacy
A good VPN like NordVPN has a no-log policy, which means that they do not track and store your information. Also, they never disclose your activity to a third party.
Whereas, the free proxy may monitor your online activity and sell your information to a third party.
Proxy is more costly than VPN
If you need a proxy server for more than one application or browser, then it may cost you more. But, with VPN, there is no limitation, and thus the cost is affordable.
The best three VPN to use are: NordVPN, Express VPN and SurfSark VPN.
Do you need a proxy server if you have a VPN?
Well, it depends upon your usage.
If you like to access websites from browsers, or like to do any type of transaction, want to establish peer to peer connection, secure video streaming, then VPN is the best.
But, if you like to scrape web content, access secure websites, and to use for bots like Sneaker bots, Twitter bot, Instagram bot, YouTube bot, then the proxy is best.