FTC disclaimer: This post contains affiliate links and I will be compensated if you make a purchase after clicking on my link.
With increasing cybercrimes, preventing unauthorized access and malicious activity is challenging.
Many organizations and individuals would like to protect information from unwanted and unauthorized sources.
Many tools provide different security levels and secure private data. Further, you can also enhance security through a strong password and multi-factor authentication.
The most famous security tool is the Firewall that protects and secures devices from an external network like the Internet.
Firewalls act as a shield to protect your network and prevent threats and risks involved with the Internet.
Moreover, the Firewall will scan incoming and outgoing traffic from one network to another.
Let’s look into what is a Firewall and how a Firewall protects your private network from unwanted traffic and unauthorized access.
What is Firewall?
A firewall is a network security system that protects, control, and monitors network traffic and unauthorized access on preset security parameters.
Furthermore, a firewall is a software program, hardware device, or the combination of two that acts as a filter for incoming or outgoing traffic.
It acts as a security guard that protects your private network from malicious activity and reduces the risk and threat involved from the public network.
In other words, a Firewall establishes a barrier or wall between your private or internal network and external or public network to block malicious traffic like viruses and hackers’ attempts.
Moreover, a firewall is considered as the first line of defense in network security that can allow or block specific traffic based on a set of security rules.
Why do you need a Firewall?
Your system or computer is vulnerable when you have access to a high-speed Internet connection.
The high-speed Internet connection can be your broadband connection, WiFi network in a park, airport, or cafe.
Also, the high-speed Internet connection is always an active connection that provides limited control and protection to your system.
As a result, your system or internal network is more vulnerable and insecure to external networks like the Internet.
Firewall implementation will create security policies that protect your network system from harmful threats.
Further, it will reduce the repeated exposure to threats like online fraud, identity theft, malware, and hacking.
The Firewall will develop proactive protection to the worst danger by implementing an invisible wall or shield.
What does a firewall do?
The Firewall performs the following task:
- It will defend sensitive resources
- The Firewall will validate access to your system
- It will manage and control network traffic
- The Firewall will act as a shield or intermediary between two networks
- The Firewall will keep a record of connections and report on events
You can think of Firewall as a gatekeeper and traffic controller.
As a gatekeeper, a Firewall will block unwanted traffic and unauthorized access to your operating system.
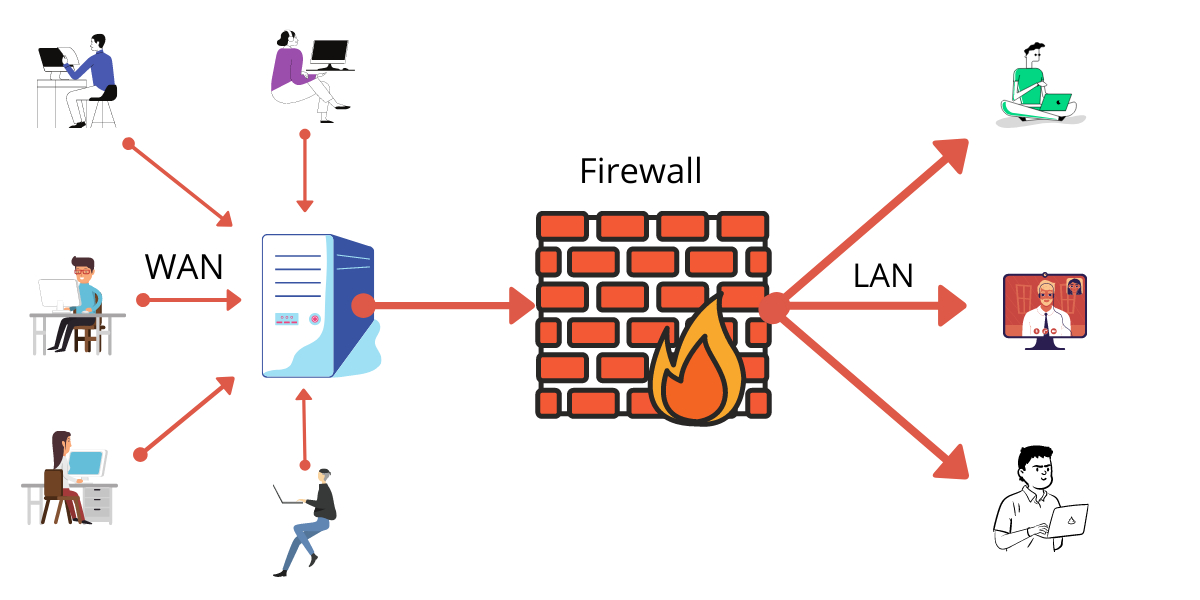
It will implement a barrier or filter between your computer and a Wide Area Network (WAN) such as the Internet.
As a traffic controller, the Firewall will manage your incoming or outgoing traffic and prevent access to sensitive information.
Further, it will block unsolicited incoming traffic that exposes malicious web activity like malware and hackers.
It is required that your operating system come with a pre-installed Firewall, and it should be configured appropriately to run updates automatically.
How does a Firewall work?
A Firewall security system will analyze your incoming or outgoing traffic based on preset rules.
You need to configure your Firewall to allow and accept those incoming connections or data packets that are safe and follow security rules.
It will act as a shield at your computer’s entry point or port or devices like routers.
The computer or device is identified through an IP address, just like how your postal address identifies where you live.
When you have configured your Firewall and provided the preset rules, the Firewall will create “Chokepoints” to analyze your incoming traffic.
Moreover, the Firewall will also create audit logs for your connection and network traffic.
Additionally, you can enhance Firewall security with various types of signatures and host conditions to control network traffic.
Also, you can have granular control over what type of system process and function can have access to network resources.
Overall, the Firewall will safeguard your computer or host and implement Access Control Policy Enforcement Point (PEP).
Different types of Firewall?
There are different types of firewalls based on structure and functionality, which can be installed in devices to protect networks and computers.
The Firewall installation will depend on the user’s usage and requirement.
There could be hardware-based firewalls, software-based firewalls, and cloud-based firewalls.
The hardware-based Firewall is like a broadband router installed between your internal network and gateway.
The software-based Firewall is installed inside your computer system, which works with application and port numbers.
Lastly, cloud-based firewalls are more advanced firewalls that protect an organization and update security levels as needed.
The most common example of a cloud-based Firewall is Firewall as a Service (FaaS)
Let’s look into a different type of Firewall available for users.
Packet-filtering firewalls
Packet-filtering firewalls are the most common and oldest type of firewalls that protect your system by filtering network traffic packets.
If the network packet is not according to the pre-defined rules, it will be dropped.
The network packets are smaller bits of data that contain information in the header.
The header of the packets depicts the address of the packets, port number, and the connection protocol.
The address of the packets will be the IP address of the source and destination server or computer.
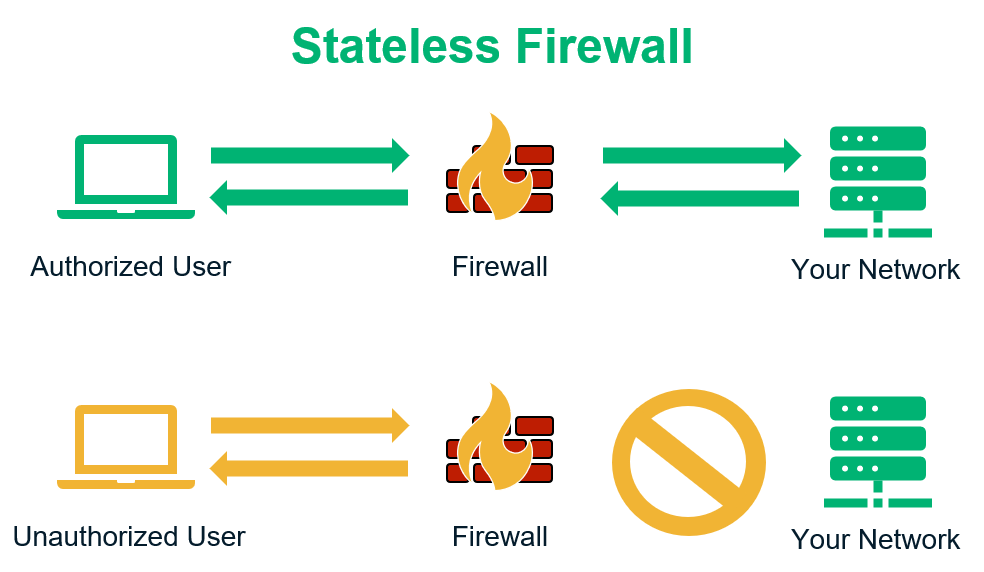
The Packet-filtering firewalls come in two different categories: stateful and stateless.
The stateful packet-filtering firewalls will analyze the packets within the context of network connection. On the other hand, stateless packet-filtering firewalls will analyze packets in isolation.
Packet-filtering firewalls are low cost, suitable for smaller networks, and limited security.
Moreover, Packet-filtering firewalls will work only on the network layer of the TCP/IP model and would be vulnerable to spoofing. It doesn’t protect you from web-based traffic.
You can protect and detect malicious requests through advanced firewalls like proxy or Next-Generation firewalls.
Proxy Firewalls
Proxy Firewalls serve as a gateway firewall between your internal and external networks like the Internet.
It will protect your internal network by applying a message filtering technique at the application layer of the OSI model.
Further, it is equipped with technology to inspect and analyze incoming network packets.
In other words, proxy-based firewalls prevent threats and malicious traffic between the client and server.
The proxy firewalls work on HyperText Transfer Protocol (HTTP) and HTTPS (HyperText Transfer Protocol Secure) levels.
The biggest drawback of Proxy firewalls is that they may face latency problems at the time of heavy traffic.
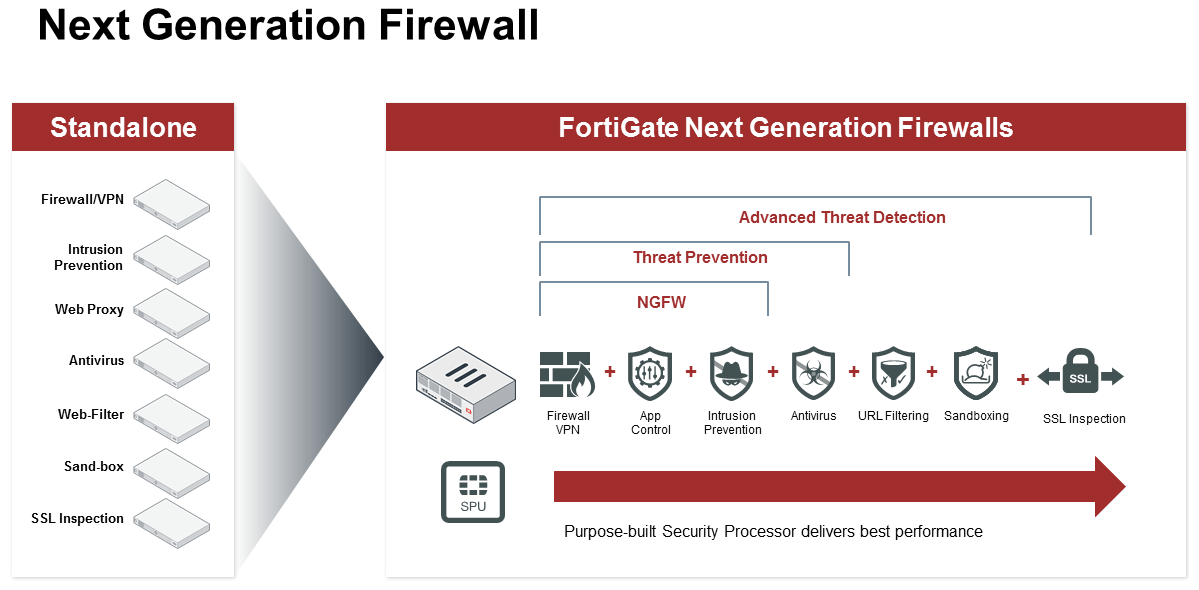
Next-generation firewalls (NGFW)
Next-generation firewalls analyze the deeper aspects of the packets’ header and inspect the packet’s content.
If Next-generation firewalls find the connection dangerous, it will block the packets and prevent access to the application like browser or online video game.
The functionalities of Next-generation firewalls include antivirus software, intrusion prevention systems, encrypted traffic inspection, cloud-delivered threat intelligence, and more.
Further, it will block and neutralize modern threats like advanced malware and application-layer attacks.
Let’s look into some of the essential features of Next-generation firewalls.
Deep packet inspection (DPI)
Deep packet inspection is a filtering technique that proceeds with in-depth analyses and inspection of packets.
It does a deeper inspection of the packet’s payload and analyzes which application receives the packages.
Identity awareness
Identity awareness is the rule-based restriction that allows traffic access to the listed computers, logged-in users, and more.
Application awareness
Application awareness enables the Firewall to take logs of the running application and the ports those applications are using.
It protects those applications from malware attacks that can stop the running process and hijack the ports.
Sandboxing
Sandboxing is functionality in Firewall that tests the incoming code in a separate environment before processing it to users.
It will check whether the packets contain malicious content or not.
Stateful Multilayer Inspection (SMLI) Firewalls
Stateful Multilayer Inspection Firewalls inspect incoming data packets from harmful threats. It involves data inspection technology and TCP handshake verification.
Moreover, this type of Firewall will also keep track of established connections.
When used for the first time, devices will establish connection and request data, then SMLI will create a database known as a state table.
The state table contains information like source and destination IP address, port number, and more. Further, it will store the connection information for each session.
The stored information for each open connection analyzes incoming and outgoing data.
Also, SMLI will examine the entire packets and allow them to pass through each layer, such as network, transport, and application layers of the TCP/IP model.
The complete examination of the packets and connection will determine the communication state. It will ensure and verify the initiated communication take place from trusted sources.
Stateful Multilayer Inspection (SMLI) Firewalls are considered safer and secure firewalls.
The drawback of stateful inspection firewalls is that they track statistics of all incoming traffic. In contrast, it will put more pressure on computer resources and thus slow down the data packets speed.
Network address translation (NAT) firewalls
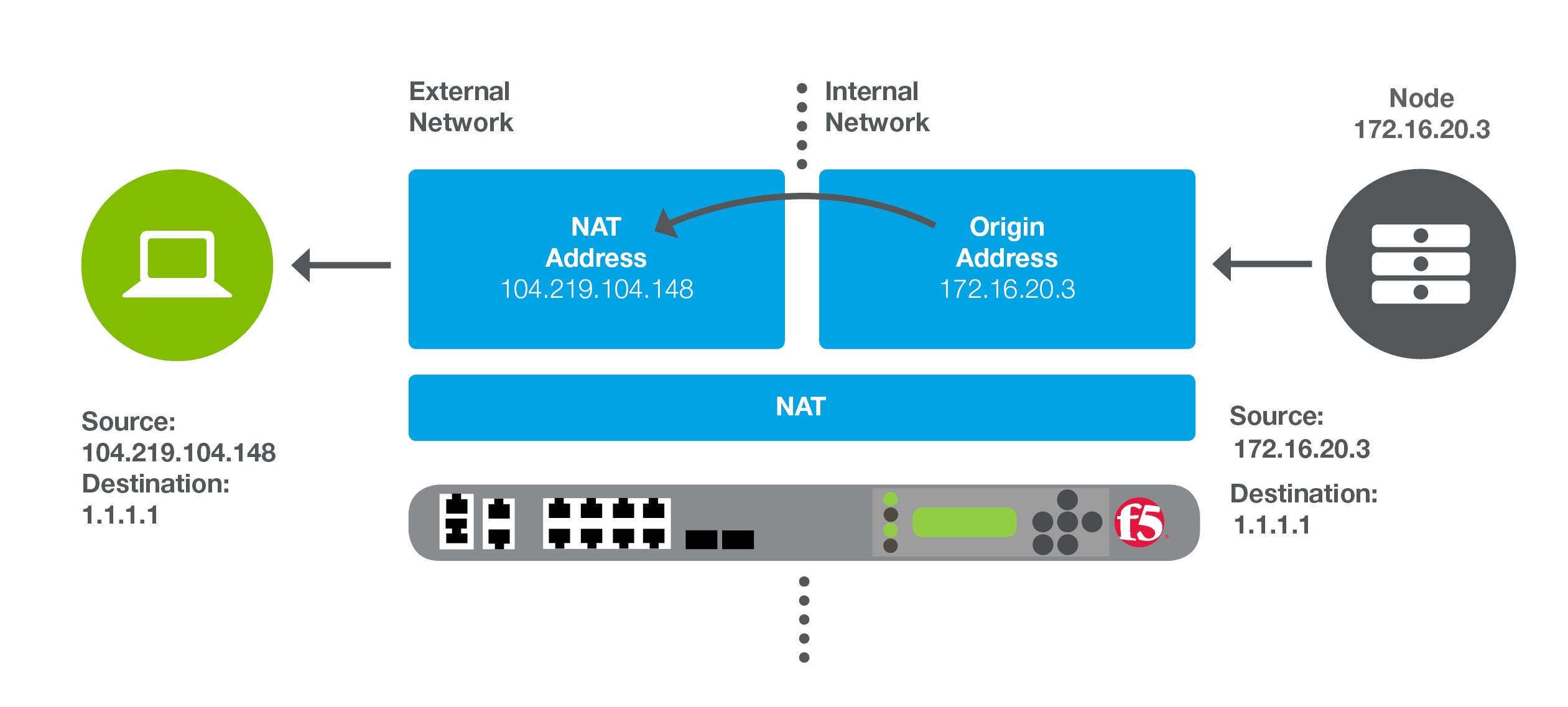
Network address translation firewalls allow multiple devices in a network to connect with an external network like the Internet using a single IP address.
The devices’ private or internal IP addresses are hidden and safe from attackers.
When the Internet connection is established, then NAT firewall will create a unique IP address and hide the individual IP address of the devices.
As a result, it protects the individual IP address of the devices from attacker scanning to get access to the private IP address of the devices.
Unified threat management (UTM) firewalls
Unified threat management firewalls enhance security by incorporating several security features in a single dashboard.
It provides solutions by combining the features of stateful inspection firewall with antivirus, intrusion prevention system (IPS), Virtual Private Network (VPN), anti-spam and more.
It also includes cloud management services to provide simplicity and ease of use.
The organization implements Unified threat management (UTM) firewalls as a single security solution to manage multiple security functions.
Further, it creates a robust system and ensures complete protection against unwanted cyber threats.
Unified threat management firewalls reduce complexity and overhead and pull all security solutions into a single umbrella.
It is beneficial for those who like to protect their network with limited resources or staff.
Thread-focused NGFW
Thread-focused NGFW is the advanced version of traditional NGFW, which focuses on threat detection and neutralization.
It possesses intelligent security automation, creating security rules and policies to increase the overall defense system.
Further, it will continuously analyze and monitor the suspicious activity of the incoming traffic.
Moreover, it will also record previous data and analyze any change in behavior patterns.
The quick and advanced threat detection functionality reduces the overall threat and keeps your system clean.
Web application firewalls (WAF)
Web application firewalls help in protecting applications from malicious users.
Unlike Web application firewalls, the traditional firewalls protect private networks from malicious applications.
Web application firewalls are installed in between web applications and the Internet.
It will protect, filter, and monitor the HTTP traffic from SQL injection, cross-site forgery, cross-site-scripting (XSS), file inclusion, and more.
Circuit-level Gateways Firewall
Circuit-level Gateways Firewall works on the session layer of the OSI model.
However, the process of Circuit-level Gateways Firewall starts after verification of TCP (Transmission Control Protocol) connections and sessions establishment.
It ensures that the sessions are protected and safe to continue. The advantage of Circuit-level Gateways Firewall is that it doesn’t consume many resources.
The disadvantage of a Circuit-level Gateways Firewall is that it is not considered safe to protect the system.
Unlike packet filtering firewalls, it does not inspect and analyze network packets; instead, it examines the information only about transactions.
So, if the TCP connection is verified, but the data packets contain malware, it will pass through the Firewall.
Firewalls as a Service (FaaS) or Cloud Firewalls
Firewalls as a Service are cloud-based firewalls typically operated and maintained on the Internet.
Third-party vendors carry out cloud Firewalls, and the functionality is very similar to Proxy Firewalls.
The advantage of Firewalls as a Service is that it is easy to configure and scalable as per the requirement. Further, there is no overhead and maintenance of resources.
Firewalls as a Service is very useful for organizations that filter out additional traffic, secure internal networks, and protect cloud infrastructure.
Which Firewall is best?
The selection of a Firewall depends on the requirement of an individual or organization. Also, the different types of firewalls protection vary.
Moreover, you can use more than one Firewall to protect your network and resources.
For instance, an organization can use cloud firewalls to protect the different perimeters of the network, and an individual can use personal firewall software on the computer system to protect assets.
The proper selection of a Firewall can depend on the following factors:
Organization size
If the organization is big enough, they need firewalls architecture to protect internal networks and assets.
Resource availability and multilayer protection
If the organization has many resources, it can afford a multilayer firewall that can protect and filter incoming and outgoing traffic.
Further, it will analyze network security and protect the application level’s assets.
Do you need firewalls at home?
The Firewall is considered a first defense in the home network security system.
You must install a Firewall at your wireless router.
Next, you can install a software-based Firewall on your devices connected with your home network.
It would help if you also had a good antivirus, regular operating system updates, web browsers, and software.
The history of firewalls
The developer has started the first firewalls project in late 1980, and they developed the first Firewall to protect data packets.
The data packets firewalls inspect the incoming and outgoing data packets on the Network and Transport layer of the OSI model.
Further, it helps in the protection of data packets from malware attacks.
The Next Generation Firewalls (NGFW) and Stateful Firewalls were introduced in mid-1990 to protect the network in the application layer of the OSI model.
With the increased vulnerability exploitation in the application layer, they developed advanced protection like Intrusion Prevention Systems Products (IPS) in early 2000.
Next, Cloud-based firewalls were developed in early 2010 to filter and protect network traffic primarily deployed in the organization.